Wireless networks have become essential infrastructure in our connected world. Many organisations harbour misconceptions about wireless security that can lead to serious vulnerabilities. Understanding the truth behind these wireless security myths helps security professionals implement proper protections. This article exposes common misconceptions and provides factual information about Wi-Fi security.
Table of Contents
Common Wi-Fi Security Misconceptions
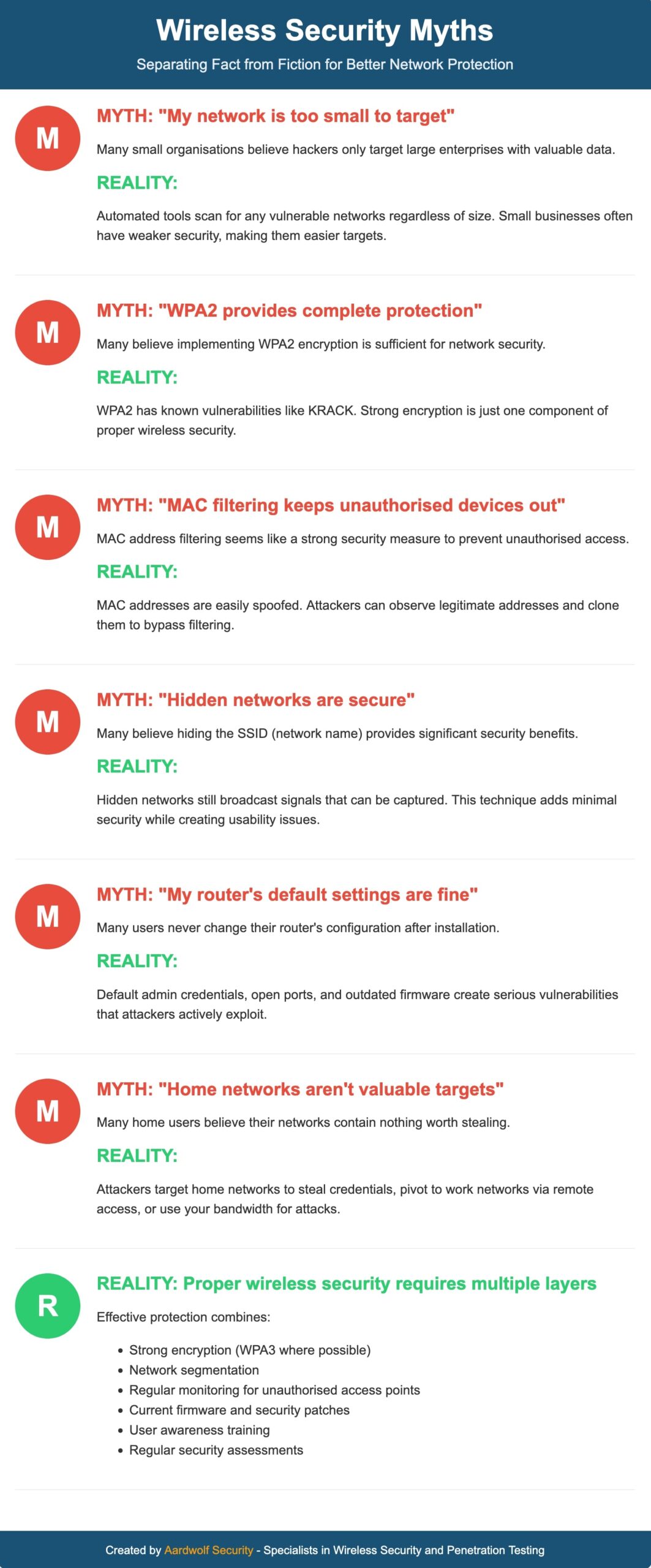
“Home Networks Aren’t Targets”
Residential users often believe their networks hold no value to attackers. This dangerous myth creates security complacency in home environments.
Cybercriminals actively target home networks for multiple reasons. They can pivot to corporate networks via remote access connections, harvest credentials from multiple services, or use your bandwidth for malicious activities. Home networks often contain valuable personal and financial information.
Remote work increases these risks as corporate data traverses home networks. Strong home network security has become essential for both personal and organisational protection.
“WPA2 Provides Complete Protection”
Many administrators believe implementing WPA2 encryption provides complete network security. While WPA2 offers significant protection over previous standards, it has vulnerabilities attackers can exploit.
The KRACK (Key Reinstallation Attack) vulnerability demonstrated WPA2’s weaknesses in 2017. This attack allowed interception of previously encrypted traffic. Other vulnerabilities, like dictionary attacks against weak passwords, remain effective against WPA2 networks.
WPA3 improves security but isn’t universally implemented. A comprehensive approach combines strong encryption with additional security layers for proper protection.
# Example WPA2 vulnerability scan using Aircrack-ng
sudo airmon-ng start wlan0
sudo airodump-ng wlan0mon
sudo aireplay-ng --deauth 10 -a [TARGET_BSSID] wlan0mon
sudo airodump-ng -c [CHANNEL] --bssid [TARGET_BSSID] -w output wlan0mon
sudo aircrack-ng output*.cap -w wordlist.txt“MAC Filtering Keeps Unauthorised Devices Out”
MAC address filtering appears to provide security by allowing only registered devices on a network. This approach has significant limitations that make it ineffective as a primary security measure.
Attackers can easily observe legitimate MAC addresses through passive monitoring. They can then clone these authorised addresses to bypass filtering controls. This technique, called MAC spoofing, requires minimal technical skill.
MAC filtering also creates administrative burdens when managing legitimate devices. A combination of multiple security layers provides much better protection than relying on MAC filtering alone.
Debunking Wireless Security Assumptions
“Public Wi-Fi Is Safe with a Password”
Many users assume a password-protected public Wi-Fi network provides adequate security. This assumption creates dangerous risks when accessing sensitive information in public spaces.
Password-shared networks allow all connected users to potentially monitor others’ traffic. Attackers on the same network can intercept unencrypted communications using simple tools. Even encrypted websites may be vulnerable to sophisticated attacks.
Public Wi-Fi should always be treated as untrusted. VPNs provide essential protection by encrypting all traffic between your device and the VPN server.
# Setting up a simple Man-in-the-Middle attack on public Wi-Fi
sudo apt-get install ettercap-graphical
sudo ettercap -G
# Select "Sniff" > "Unified sniffing"
# Select interface (e.g., wlan0)
# Select "Hosts" > "Scan for hosts"
# Select "Hosts" > "Host list"
# Select target IP addresses
# Select "Mitm" > "ARP poisoning"
# Select "Sniff remote connections"“Our Wireless Network Is Hidden and Secure”
Hiding your SSID (network name) seems like a sensible security precaution. However, this approach provides minimal actual security benefits while creating usability problems.
Hidden networks still broadcast probe requests and responses. These signals can be captured by attackers using standard wireless monitoring tools. The network name remains visible in these transmissions.
Hidden networks often create connectivity issues for legitimate users. Strong encryption and proper authentication provide much more effective security than SSID hiding.
“Strong Passwords Are Enough for Wi-Fi Security”
Using a strong Wi-Fi password represents good practice but cannot provide complete network protection. Passwords alone don’t address all potential attack vectors against wireless networks.
Attackers can capture handshake information without needing immediate password access. This data can be analysed offline at their convenience. Password-based authentication also doesn’t protect against rogue access points or evil twin attacks.
Comprehensive security requires multiple measures including network segmentation, intrusion detection, and regular security assessments through WiFi penetration testing.
Wi-Fi Safety Facts vs Myths
Myth: “Wireless Signals Can’t Be Accessed from Outside”
A common belief suggests Wi-Fi signals remain confined within building walls. This misconception leads to inadequate security planning and potential exposure.
Standard Wi-Fi signals can travel hundreds of metres in optimal conditions. Specialised antennas can capture signals from even greater distances. Building materials provide inconsistent signal blocking.
Network planning should assume signals extend beyond physical boundaries. Proper signal mapping helps determine actual coverage areas and potential exposure points.
Fact: “Default Settings Create Vulnerabilities”
Factory default configurations prioritise ease of setup over security. Manufacturers often implement minimal security to reduce customer support issues.
Default passwords, outdated firmware, and unnecessary services create exploitable weaknesses. These settings rarely align with security best practices or organisational requirements.
Every new wireless device needs configuration review and hardening before deployment. This process should include password changes, firmware updates, and disabling unnecessary features.
Myth: “Guest Networks Are Always Safe”
Many organisations believe guest networks automatically isolate visitor traffic from internal systems. This assumption can lead to significant security exposures without proper configuration.
Default guest networks may share infrastructure with primary networks. Without correct VLAN implementation, traffic separation might be incomplete. Guest networks require the same security considerations as primary networks.
Proper guest network implementation should include bandwidth limitations, session timeouts, and complete isolation from internal resources.
“My Router’s Default Settings Are Fine”
Many users never change their router’s default configuration after installation. This oversight creates serious security vulnerabilities that attackers actively exploit.
Default admin credentials remain publicly available for most router models. These known username and password combinations provide easy access to router administration. Unchanged settings often include unnecessary open ports and services that expand attack surfaces.
Proper router configuration requires changing default credentials, disabling unnecessary services, updating firmware, and configuring appropriate security features. These steps significantly improve security compared to default settings.
“Firewalls and Antivirus Protect My Wi-Fi”
A common misconception suggests that device-level protections like firewalls and antivirus software secure the wireless network itself. This assumption creates dangerous security gaps.
These tools protect individual devices but not the network infrastructure. If your router becomes compromised, all traffic—including that from protected devices—can be intercepted or redirected. Network-level attacks often bypass device protections entirely.
Comprehensive security requires both device-level and network-level protections working together. Router security remains essential even when endpoints have strong protection.
“Guest Networks Don’t Need Security”
Many organisations deploy guest networks with minimal security controls. This approach creates unnecessary risks that can impact the entire network environment.
Inadequate guest network isolation can allow unauthorised access to internal resources or IoT devices. Attackers can use these connections to pivot into more sensitive areas. Unsecured guest networks may also enable bandwidth abuse and malicious activity from your IP address.
Properly secured guest networks should include traffic isolation, bandwidth limitations, content filtering, and session timeouts. These controls balance accessibility with essential security requirements.
“Enterprise-grade Routers Are Immune”
Business-grade wireless equipment carries a perception of invulnerability that creates false security confidence. This misconception leads to inadequate security practices.
Even high-end equipment faces vulnerabilities requiring patching and proper configuration. Many enterprise Wi-Fi deployments suffer from implementation weaknesses rather than equipment limitations. Regular security assessments remain necessary regardless of equipment quality.
Enterprise networks benefit from advanced features but require proper implementation, monitoring, and maintenance to provide effective security.
Is WPA3 completely secure against all wireless attacks?
While WPA3 provides significant improvements over WPA2, including stronger encryption and protection against offline dictionary attacks, it isn’t immune to all threats. Security researchers have already identified some vulnerabilities in WPA3 implementations.
A comprehensive security approach still requires multiple protective layers beyond encryption alone.
Can attackers really access my Wi-Fi from outside my building?
Yes, standard Wi-Fi signals can travel hundreds of metres in optimal conditions. Building materials provide inconsistent signal blocking, and specialised directional antennas can capture signals from even greater distances.
Always assume your wireless signals extend beyond your physical boundaries.
Does using a VPN completely protect me on public Wi-Fi?
VPNs provide essential encryption for public Wi-Fi use, but they don’t address all risks. VPNs protect data transmission but not the device itself. Your device remains vulnerable to direct attacks if it has unpatched vulnerabilities or if malware exists on the network.
VPNs should be part of a multi-layered security approach.
Is it true that changing default passwords is enough to secure a wireless router?
Changing default passwords is an essential first step but insufficient for complete security. Routers also need regular firmware updates to patch security vulnerabilities, proper configuration of all security settings, disabling unnecessary services, and implementation of network segmentation where appropriate.
Default configurations often include open ports, UPnP, remote management, and other vulnerable services. Comprehensive router hardening addresses all these potential weaknesses.
Do wireless networks need the same level of monitoring as wired networks?
Wireless networks actually require more monitoring than wired networks in many cases. The broadcast nature of wireless communications creates unique risks including unauthorised access points, signal leakage beyond physical boundaries, and specialised wireless attacks.
Comprehensive monitoring should include both traditional network monitoring and wireless-specific tools.
Wireless Threat Awareness
Understanding Modern Attack Techniques
Wireless networks face sophisticated threats beyond simple password attacks. Understanding these techniques helps security professionals implement appropriate countermeasures.
Evil twin attacks involve creating rogue access points that mimic legitimate networks. These fake networks can intercept credentials and data when users connect. Detection requires monitoring for unauthorised access points and user awareness training.
Jamming attacks disrupt network availability by flooding wireless frequencies with interference. These attacks can precede more targeted exploitation attempts. Signal monitoring tools help identify unusual interference patterns.
Step-by-Step: Detecting Rogue Access Points
Identifying unauthorised access points represents a critical wireless security practice. Follow these steps to detect potential threats:
- Establish baseline: Document all authorised access points, including MAC addresses, SSIDs, and expected signal strengths.
- Perform regular scans: Use wireless scanning tools to identify all broadcasting networks in your environment.
# Example using Linux wireless tools sudo apt-get install aircrack-ng sudo airmon-ng start wlan0 sudo airodump-ng wlan0mon - Compare results: Identify any access points not matching your authorised baseline.
- Investigate anomalies: For each unknown access point, determine if it belongs to neighbours or represents a potential threat.
- Locate unknown devices: Use signal strength measurements from multiple locations to triangulate unauthorised access points.
# Using Kismet for AP location sudo apt-get install kismet sudo kismet -c wlan0 - Take action: Remove rogue devices or implement blocking measures through wireless intrusion prevention systems.
Regular scanning helps identify threats before they can compromise your network security.
Best Practices for Wireless Security
Implementing proper security requires understanding both threats and effective countermeasures. These best practices help organisations develop robust wireless security:
- Use current encryption standards: Implement WPA3 where possible or properly configured WPA2 with strong passwords. Avoid WEP and unencrypted networks entirely.
- Segment wireless networks: Separate guest, IoT, and corporate networks using VLANs and firewall rules. This approach contains potential breaches and limits lateral movement.
- Implement 802.1X authentication: Use certificate-based authentication where possible instead of relying solely on passwords. This approach prevents many common wireless attacks.
- Monitor wireless environments: Deploy wireless intrusion detection systems to identify unauthorised access points and unusual activity patterns. Regular scanning helps detect threats early.
- Update firmware regularly: Keep all wireless infrastructure current with security patches. Outdated firmware often contains known vulnerabilities attackers can exploit.
- Conduct regular assessments: Perform WiFi penetration testing to identify vulnerabilities before attackers discover them. External testing provides objective security evaluation.
These practices help organisations build effective security programmes that address real wireless threats.
Wireless Security in Practice
Understanding security concepts requires practical application. This video provides excellent visual demonstrations of wireless security concepts:
Effective Wireless Security Strategy
Developing an effective wireless security strategy requires addressing both technical and human factors. Security professionals should focus on these key areas:
Policy development establishes clear security requirements and acceptable use guidelines. These documents should include specific wireless security controls and user responsibilities.
Regular training helps users understand wireless risks and appropriate security practices. This education reduces the likelihood of inadvertent security compromises.
Technical controls must address the full range of wireless threats while balancing security and usability needs. Overly restrictive controls often lead users to seek workarounds that create new vulnerabilities.
Professional Wireless Security Services
Comprehensive wireless security often requires professional expertise. Penetration testing companies provide valuable external assessment of security controls and identification of vulnerabilities.
Aardwolf Security offers specialised wireless security services including:
- Comprehensive WiFi penetration testing
- Wireless architecture reviews
- Security policy development
- Incident response planning
- Security awareness training
Our team brings extensive wireless security experience to help organisations identify and address vulnerabilities before attackers can exploit them. Contact Aardwolf Security to discuss your wireless security needs.
Further Reading
For additional information about wireless security, consider these authoritative resources:
- Wi-Fi Alliance Security – Official information about Wi-Fi security standards
- NIST Special Publication 800-153 – Guidelines for Securing Wireless Local Area Networks
- Wi-Fi – Wikipedia article on Wi-Fi technology and standards
Glossary of Wireless Security Terms
- SSID (Service Set Identifier): The name of a wireless network that identifies it to users and devices
- WPA2/WPA3 (Wi-Fi Protected Access): Security protocols designed to secure wireless networks
- MAC Address: A unique identifier assigned to network interfaces for communications
- Evil Twin: A fraudulent wireless access point that appears to be legitimate
- KRACK (Key Reinstallation Attack): A vulnerability in the WPA2 protocol
- Deauthentication Attack: Forcing devices to disconnect from their wireless networks
- 802.1X: An IEEE standard for port-based Network Access Control
Wireless Security Reality Check
An infographic summarising key wireless security myths and facts: