HTTP Request Smuggling poses a serious threat to web applications. This attack tricks web servers into processing requests differently. Attackers exploit gaps between front-end and back-end servers. The technique sends crafty HTTP requests through security controls.
These attacks target the way servers handle request boundaries. Most websites use multiple servers to process user requests. A front-end server receives visitor requests first. Then it forwards these requests to back-end application servers. When these servers interpret request boundaries differently, vulnerabilities appear.
Successful attacks can bypass security controls, gain unauthorized access, and steal sensitive data. The danger comes from the hidden nature of these attacks. Many security tools fail to detect them because they review requests individually.
Table of Contents
How HTTP Request Smuggling Works
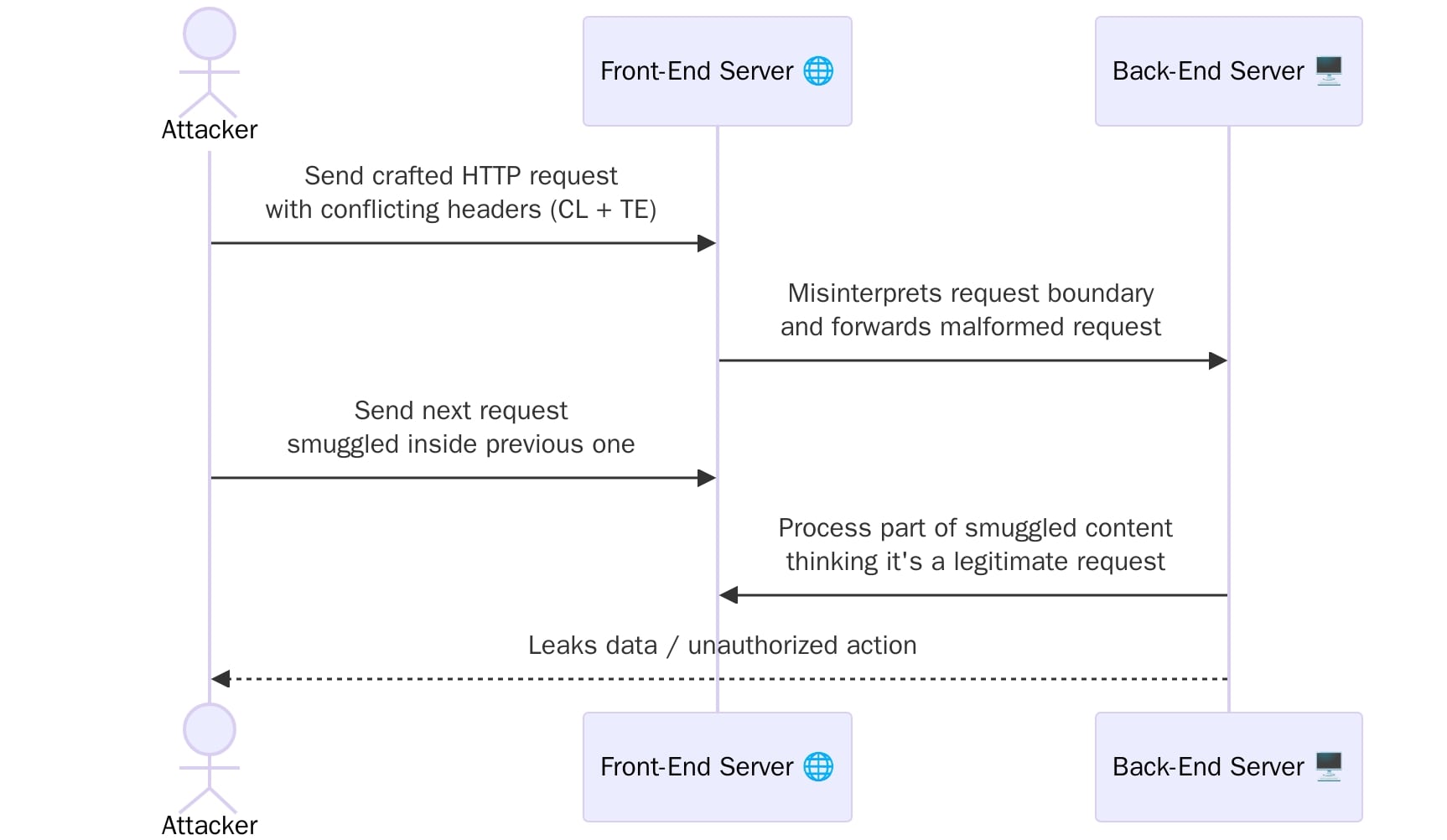
HTTP Request Smuggling attacks exploit communication problems between servers. The attack works because servers may use different methods to determine where requests end. This confusion creates security gaps that attackers can use.
When you visit a website, your browser sends HTTP requests to web servers. These servers need to know where each request ends and the next begins. Two HTTP headers help with this task: Content-Length and Transfer-Encoding.
The Content-Length header tells servers how many bytes to read. The Transfer-Encoding header uses a different method called chunked encoding. Problems arise when front-end and back-end servers prioritise different headers.
Servers can disagree about where requests end due to these different headers. The attacker takes advantage of this disagreement. They carefully craft requests that will be understood differently by each server.
Common HTTP Request Smuggling Techniques
Attackers use several techniques to exploit these vulnerabilities. The two most common methods are CL.TE and TE.CL attacks. Both methods target how servers process request headers.
CL.TE Attacks
In CL.TE attacks, the front-end server uses the Content-Length header. The back-end server uses the Transfer-Encoding header instead. This difference creates a gap that attackers exploit.
The attack works like this:
- The attacker sends a request with both headers.
- The front-end server follows the
Content-Lengthvalue. - The back-end server follows
Transfer-Encodinginstead. - Part of the request becomes hidden to security controls.
These attacks often succeed because many security tools check only the Content-Length header. The hidden part of the request bypasses these checks completely.
TE.CL Attacks
TE.CL attacks work in the opposite way. Here, the front-end server uses Transfer-Encoding while the back-end uses Content-Length. This reversal creates different but equally dangerous vulnerabilities.
The technique involves:
- Creating chunks with specific sizes in the request.
- Tricking the front-end server into processing the chunks correctly.
- Confusing the back-end server about where the request ends.
- Inserting malicious content that blends into the next request.
Both attack types can lead to serious security problems. Attackers might access private data, hijack user sessions, or bypass security controls entirely.
What Makes HTTP Request Smuggling Dangerous?
The danger of HTTP Request Smuggling comes from its stealth. The attack hides in normal-looking requests. Security tools often miss these attacks completely. Several factors make this attack especially concerning.
First, these attacks bypass many security controls. Web Application Firewalls (WAFs) might check each request individually. But they often miss problems that span across multiple requests.
Second, the attack can poison web caches. This turns a one-time attack into an ongoing problem. Poisoned caches serve malicious content to many users without further attacks.
Third, these attacks can reveal sensitive data. Attackers might access other users’ information, authentication tokens, or cookies. This access happens because request boundaries get mixed up.
Finally, HTTP Request Smuggling creates entry points for other attacks. Cross-site scripting, SQL injection, and server-side request forgery become easier after a successful smuggling attack.
How Can You Detect HTTP Request Smuggling?
Detecting HTTP Request Smuggling requires careful testing. Several methods help find these vulnerabilities before attackers do. Web application penetration testing plays a key role here.
Time-based detection offers one reliable approach. This method sends requests that should cause delays if vulnerabilities exist. Measured response times reveal potential problems. Unusual delays suggest that request smuggling might work.
Another method uses differential responses. The tester sends special requests and watches how servers respond. Different responses to similar requests often indicate vulnerabilities. This approach requires comparing many responses carefully.
Automated tools have improved detection capabilities. Tools like Burp Suite include specific tests for these attacks. These tools can find vulnerabilities that manual testing might miss.
Regular security testing catches most request smuggling issues. Penetration testing should include specific checks for these attacks. Experts recommend testing after every major infrastructure change.
What Are Common Examples of HTTP Request Smuggling?
Real-world examples help understand how these attacks work. Several high-profile cases have shown the danger of this attack method.
Web Cache Poisoning via Request Smuggling
In this example, attackers poison web caches through request smuggling. The attack works in several steps:
- The attacker sends a crafted request with smuggled content.
- Front-end and back-end servers process the request differently.
- The smuggled part contains malicious JavaScript code.
- This code gets stored in the web cache.
- Other users receive the poisoned content when they visit the site.
This attack affects many users at once. The poisoned cache serves malicious content until administrators clear it completely.
Session Hijacking through Request Smuggling
Another common example involves stealing user sessions:
- The attacker sends a request with smuggled content.
- The smuggled part asks for another user’s session cookie.
- When that user makes a request, their cookie gets sent to the attacker.
- The attacker uses this cookie to take over the user’s session.
This attack directly targets users’ privacy and security. It allows attackers to impersonate legitimate users without their knowledge.
API Request Manipulation
API penetration testing often reveals request smuggling issues with APIs:
- An attacker identifies an API gateway with request smuggling vulnerabilities.
- They craft requests that bypass API access controls.
- The smuggled requests access restricted API endpoints.
- This access reveals sensitive data or allows unauthorized changes.
This example shows how request smuggling threatens modern API-based architectures. The attack bypasses controls that normally protect valuable data.
How Can You Prevent HTTP Request Smuggling?
Preventing HTTP Request Smuggling requires several security measures. The goal is to ensure consistent request handling across all servers. These steps help protect systems from these attacks.
Server Configuration
Proper server configuration provides the first line of defense:
- Use consistent HTTP parsing rules across all servers.
- Disable support for chunked encoding when possible.
- Configure servers to strictly validate HTTP requests.
- Use the same web server software across your infrastructure.
These changes reduce differences between front-end and back-end servers. Fewer differences mean fewer opportunities for attackers.
HTTP/2 Implementation
Moving to HTTP/2 helps prevent many request smuggling attacks:
- HTTP/2 has clearer rules about request boundaries.
- The protocol eliminates ambiguity in request parsing.
- It avoids the problems with
Content-LengthandTransfer-Encodingheaders.
While not a complete solution, HTTP/2 addresses many underlying issues. Organizations should consider this upgrade as part of their security strategy.
Regular Security Testing
Consistent security testing catches vulnerabilities early:
- Include request smuggling tests in security assessments.
- Test after infrastructure changes or updates.
- Use both automated tools and manual testing methods.
- Address found vulnerabilities quickly and thoroughly.
Security testing should check for all HTTP request smuggling variants. New attack methods appear regularly, so testing must evolve too.
Web Application Firewalls
Modern WAFs provide some protection against these attacks:
- Configure WAFs to normalize HTTP headers.
- Enable specific rules that detect request smuggling attempts.
- Update WAF rules regularly to catch new attack methods.
- Monitor WAF logs for potential attack indicators.
While helpful, WAFs should not be the only defense. They work best as part of a broader security approach.
HTTP Request Smuggling FAQs
How common are HTTP Request Smuggling vulnerabilities?
HTTP Request Smuggling vulnerabilities appear more often than many think. Research suggests that up to 10% of major websites have these issues. The problem affects many large organizations despite increased awareness.
Several factors contribute to their frequency. Complex architectures with multiple servers increase risk. Legacy systems often handle requests inconsistently. Even small configuration differences can create vulnerabilities.
Regular testing remains essential because these issues persist. New variations of the attack continue to emerge as web technologies evolve.
Can WAFs block HTTP Request Smuggling attacks?
Web Application Firewalls provide partial protection against these attacks. Most modern WAFs include rules that detect common request smuggling patterns. These rules help block obvious attack attempts before they reach servers.
However, WAFs face limitations with these attacks. Sophisticated attackers can often bypass WAF rules. The attack’s nature makes complete detection difficult because problems occur between servers, not within individual requests.
Organizations should use WAFs as one part of their defense strategy. They should not rely on WAFs alone to prevent these attacks.
What makes HTTP/2 more secure against smuggling attacks?
HTTP/2 improves security against request smuggling in several ways. The protocol uses binary framing instead of text-based messages. This approach eliminates ambiguity about request boundaries.
In HTTP/2, each request has clear beginning and end points. The protocol avoids the dual header problem that enables smuggling in HTTP/1.1. Servers process HTTP/2 requests consistently because the specification leaves less room for interpretation.
Despite these improvements, HTTP/2 implementations can still have flaws. Some implementations convert between HTTP versions incorrectly. These conversion errors sometimes create new smuggling opportunities.
How do microservice architectures affect request smuggling risk?
Microservice architectures often increase request smuggling risks. These designs typically include many services with different configurations. More components mean more potential parsing differences between services.
API gateways in microservice systems present particular concerns. These gateways route requests to various backend services. Each service might handle HTTP headers differently, creating security gaps.
Organisations using microservices need extra vigilance. They should standardize HTTP handling across all services. Regular security testing should check connections between all components.
Protecting Your Systems from HTTP Request Smuggling
HTTP Request Smuggling poses a serious threat to web applications. The attack exploits differences between servers. It bypasses security controls and can lead to data theft. Organizations must take steps to protect their systems.
Consistent server configuration provides the foundation for defense. All servers should follow the same HTTP parsing rules. Regular updates help address known vulnerabilities in web server software. Moving to HTTP/2 reduces many risks associated with request smuggling.
Security testing plays a crucial role in protection. Web application penetration testing should specifically check for these vulnerabilities. Testing must evolve as new attack methods emerge. Organizations should test their systems regularly to catch issues early.
Get Expert Help with Web Application Security
Protecting against HTTP Request Smuggling requires expertise. Aardwolf Security specializes in finding and fixing these vulnerabilities. Our team uses advanced techniques to identify security gaps before attackers do.
Our web application penetration testing service includes comprehensive checks for request smuggling. We test your entire infrastructure to find hidden vulnerabilities. Our experts provide clear guidance on fixing found issues.
Don’t wait for attackers to exploit these vulnerabilities. Contact Aardwolf Security today for a thorough security assessment. Visit our contact page to learn how we can help protect your systems from HTTP Request Smuggling and other advanced threats.