Web app security has changed greatly over the past twenty years. Early websites showed simple information with basic HTML. Users viewed content but rarely sent data back to servers. Developers built these sites with few security concerns in mind. Attacks remained fairly basic during this time.
Today’s web applications look nothing like their ancestors. Modern apps run complex code in your browser. They connect to many servers at once. Data flows between users and systems constantly. Applications stretch across clouds, containers, and devices. This growth has made security much harder to manage.
The threats have grown with the technology. Hackers once focused on simple scripts and obvious flaws. Now they use advanced tools to find subtle weaknesses. Attack methods have become more complex. Security teams face a much bigger challenge than before.
Table of Contents
How Web Applications Evolved
The Static Web (Early 2000s)
Web pages started as static documents on servers. Users requested these files through browsers. Servers sent HTML back to display information. Security focused mainly on server protection. Network firewalls handled most security needs.
Developers added simple forms to collect user input. These forms sent data back to servers for processing. This change brought new dangers to websites. SQL injection attacks became common during this period. Sites stored passwords in plain text. User data faced high risks.
The Dynamic Web (Mid-2000s)
Websites became more interactive around 2005-2010. JavaScript gained popularity among developers. AJAX allowed parts of pages to update without full reloads. Users enjoyed richer experiences on these sites.
Security problems grew along with these features. Cross-site scripting (XSS) attacks spread widely. Session hijacking threatened user accounts. The OWASP Top 10 list emerged to guide developers. Security awareness increased but implementation lagged behind.
The Application Era (2010-2015)
Web sites transformed into full applications around 2010. Single-page applications changed how code worked. Frameworks like Angular and React gained adoption. Mobile apps connected to the same systems. The term “web application” became standard.
Security challenges multiplied during this shift. APIs exposed more attack surfaces. Cross-Origin Resource Sharing created new risks. Authentication became more complex. Developers struggled to secure these advanced systems.
Today’s Distributed Web (2015-Present)
Modern web applications span multiple environments and technologies. Microservices break applications into small parts. Containers hold code that moves between systems. Cloud services provide key functions. Applications connect through complex API networks.
The security landscape has grown enormously complex. Traditional boundaries between systems have disappeared. Data flows through many services and providers. Attack surfaces have expanded beyond recognition. Old security models cannot protect these systems.
How the Threat Landscape Changed
Early Threats: Simple But Effective
Early web attacks targeted obvious weaknesses in code. SQL injection allowed access to databases. Cross-site scripting inserted malicious code. Session hijacking stole user identities. These attacks worked through basic input handling flaws.
Attackers needed limited skills to exploit these problems. Tools remained fairly simple during this era. Defense focused on fixing code issues. The security community developed early testing methods. OWASP published its first Top 10 list in 2003.
Middle Period: Growing Sophistication
Attack methods grew more advanced between 2005-2015. Cross-site request forgery manipulated trusted sessions. XML external entity attacks targeted parsers. Insecure deserialization exploited object conversion. These attacks required deeper technical knowledge.
Attackers developed better tools during this period. Automated scanning became more common. Exploit frameworks made attacks easier. Defense shifted toward secure coding practices. Web application firewalls gained popularity.
Modern Threats: Complex and Persistent
Today’s threats target the distributed nature of applications. API vulnerabilities expose core functions. Supply chain attacks compromise dependencies. Client-side attacks bypass server protections. Cloud misconfigurations open new doors.
Modern attackers use sophisticated techniques and patience. They chain multiple smaller flaws together. They target identities across systems. Defense requires multiple layers and approaches. Security must span the entire development lifecycle.
Major Security Trends Over Two Decades
OWASP Top 10 Evolution
The OWASP Top 10 shows how web app security risks changed over time. Early lists focused on injection and simple flaws. Recent lists include API security and supply chain concerns. Some risks remained constant through all versions.
Injection attacks topped the list for many years. Authentication flaws consistently appear in all versions. Newer risks reflect changing technology landscapes. The 2021 list includes categories not imagined in 2003.
Shifting Security Left
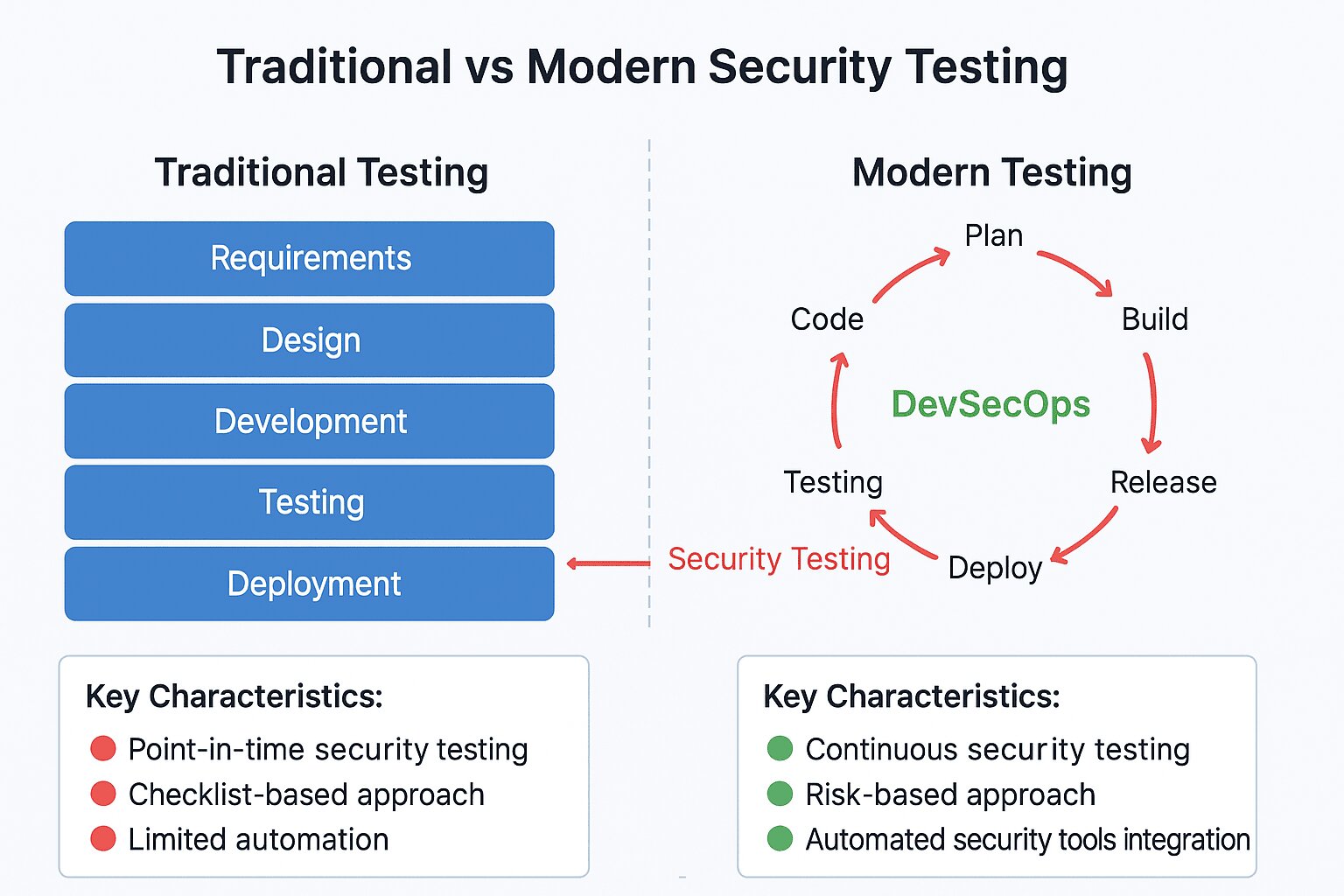
Security has moved earlier in development processes. Early web security happened after code deployment. Testing occurred at the end of projects. Issues discovered late caused project delays.
Modern approaches integrate security from the beginning. Developers receive security training before coding starts. Automated tools check code as it’s written. This “shift-left” approach catches problems earlier.
The Rise of DevSecOps
Development and operations merged through DevOps practices. Security joined this movement with DevSecOps. Teams now build security into automated pipelines. Continuous testing happens throughout development.
This approach suits modern web application needs. Fast-moving projects maintain security standards. Automated checks prevent common problems. Security becomes everyone’s responsibility rather than one team’s job.
What Has Penetration Testing Learned?
From Checklist Testing to Risk-Based Approaches
Early pentesters followed simple vulnerability checklists. They looked for known issues in predictable places. Reports focused on counts of findings. This approach missed contextual problems.
Modern penetration testing takes a risk-based approach. Testers understand business context and priorities. They focus on realistic attack scenarios. Testing covers entire workflows rather than isolated components.
Manual vs. Automated Testing Evolution
The balance between human and machine testing has shifted. Early testing relied heavily on manual checks. Tools provided limited coverage of issues. Experienced testers found problems through intuition.
Today’s approach combines automation with expert analysis. Tools handle repetitive checks and coverage. Human testers focus on logic and business flaws. This combination provides deeper security insights.
Common Web Security Questions?
How Has the OWASP Top 10 Changed?
The OWASP Top 10 reflects security trends over twenty years. Injection attacks remained at the top for many years. Broken authentication consistently ranks high. Newer lists include API security concerns.
The 2021 list added categories for supply chain risks. It consolidated some previously separate categories. It emphasized the changing nature of web applications. These changes show how security priorities have evolved.
How Does API Security Differ From Traditional Web Security?
API penetration testing focuses on different areas than traditional web tests. APIs expose direct access to functions and data. They often bypass front-end protections. Authentication happens through tokens rather than sessions.
API testing examines authorization at a granular level. It checks data validation between systems. It verifies rate limiting and resource protections. These tests require specialized knowledge of API protocols.
How Do Cloud-Native Applications Change Security Testing?
Cloud environments create unique security challenges for testing. Resources may exist temporarily during testing. Services connect through managed identities. Configuration settings affect security posture.
Testers must understand cloud provider security models. They check for misconfigurations in cloud services. They verify identity management between components. Traditional network boundaries don’t apply in these environments.
What Impact Has DevSecOps Had on Web Security?
DevSecOps practices have changed how security testing works. Tests run automatically with each code change. Results feed directly to development teams. Security becomes part of quality criteria.
This approach catches issues before they reach production. It integrates security into development culture. It provides continuous feedback rather than point-in-time assessments. Security improves through constant reinforcement.
How Has Client-Side Security Evolved?
Client-side security has grown increasingly important. Early web security focused mainly on servers. Modern applications run significant code in browsers. This shift has created new threat vectors.
JavaScript supply chains pose substantial risks. Third-party scripts may access sensitive data. Client-side input validation must complement server checks. Content Security Policy helps control these risks.
The Future of Web Security
Web app security continues to evolve rapidly. Several trends point to future directions. Security teams should prepare for these changes.
Zero Trust models will replace perimeter-based security. Every request will require verification regardless of source. Identity will become the primary security boundary. This approach suits distributed modern applications.
Artificial intelligence will change both attacks and defenses. Automated tools will find more subtle vulnerabilities. Defensive systems will detect unusual patterns faster. The speed of security responses will increase.
Development and security will continue merging together. More security checks will happen during coding. Developers will take greater responsibility for security. The gap between building and securing will narrow further.
Protect Your Web Applications with Expert Help
Modern web applications face complex and evolving threats. Web application penetration testing provides essential protection against these risks. Expert testers find vulnerabilities before attackers can exploit them.
Aardwolf Security specialises in modern web app security testing. Our team understands the latest threats and technologies. We provide actionable recommendations based on real-world risks.
Don’t leave your applications exposed to evolving threats. Contact Aardwolf Security today for comprehensive web app penetration testing.