Default credentials represent one of cybersecurity’s most persistent threats. These factory-set usernames and passwords create critical vulnerabilities across countless systems worldwide. Understanding these risks helps organisations strengthen their security posture effectively.
Every device manufacturer ships products with preset login details. These credentials enable initial system access and configuration. However, many administrators never change these settings, leaving systems exposed to attackers.
Table of Contents
Understanding Default Credential Vulnerabilities
Default credentials pose significant security risks across multiple system types. Network devices, IoT sensors, and web applications commonly ship with standard login combinations. Attackers maintain extensive databases containing thousands of these preset credentials.
The vulnerability stems from predictable authentication patterns manufacturers use. Common combinations include “admin/admin,” “root/password,” and device-specific variants. These patterns make systems vulnerable to automated attacks and manual exploitation attempts.
Password security weaknesses multiply when organisations deploy multiple devices with identical credentials. A single compromised device can provide attackers with access keys to entire network segments.
Example of Real-World Default Credentials
| Device/System | Username | Password |
|---|---|---|
| Cisco Routers | cisco | cisco |
| D-Link Cameras | admin | (blank) |
| HP Printers | admin | admin |
| Linksys Routers | admin | admin |
| MySQL Database | root | (blank) |
| Netgear Routers | admin | password |
| Oracle Database | system | manager |
| PostgreSQL | postgres | password |
| Raspberry Pi | pi | raspberry |
| QNAP NAS | admin | admin |
| Synology NAS | admin | (blank) |
| Tomcat Server | tomcat | tomcat |
| VMware vCenter | administrator | vmware |
| Xerox Printers | admin | 1111 |
Attack Vectors and Exploitation Methods
Cybercriminals employ various techniques to exploit default credentials systematically. Automated scanning tools identify vulnerable devices across network ranges rapidly. These tools test common credential combinations against discovered services continuously.
Credential stuffing attacks leverage lists of known default passwords against target systems. Attackers combine these lists with device fingerprinting to maximise success rates. Web application penetration testing often reveals these vulnerabilities during security assessments.
Manual exploitation techniques focus on high-value targets requiring careful reconnaissance. Attackers research specific device models to identify applicable default credentials. This approach proves particularly effective against custom or enterprise-grade equipment.
IoT Security and Default Password Risks
IoT devices present particularly challenging default credential scenarios for modern organisations. These devices often lack robust security features or update mechanisms. Manufacturers prioritise ease of deployment over security considerations frequently.
Smart cameras, sensors, and controllers typically use weak authentication schemes. Many devices never receive security updates throughout their operational lifespans. This creates persistent vulnerabilities that attackers can exploit indefinitely.
The scale of IoT deployments amplifies default credential risks significantly. Organisations may deploy hundreds of identical devices simultaneously. Each device represents a potential entry point for malicious actors.
Vulnerability Statistics
See the following Shodan search for default credentials which returns a huge amount of publicly available results:
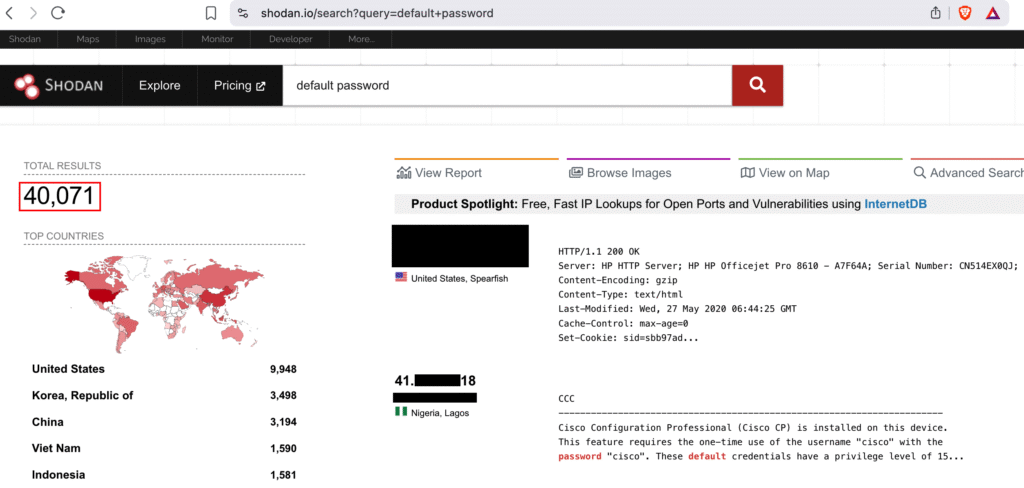
Research indicates that over 60% of IoT devices retain factory default passwords. This statistic represents millions of vulnerable endpoints across global networks. The problem continues growing as IoT adoption accelerates across industries.
Network Security Implications
Default credentials create cascading security failures across network infrastructures. Compromised devices often provide lateral movement opportunities for attackers. Network segmentation becomes ineffective when multiple devices share identical authentication credentials.
Network penetration testing services frequently identify default credential vulnerabilities as primary attack vectors. These assessments reveal how single compromised devices can compromise entire network segments.
Administrative access gained through default credentials enables privilege escalation attacks. Attackers can modify configurations, install malicious software, and establish persistent access channels. The impact extends beyond individual devices to encompass entire network infrastructures.
Step-by-Step Attack Scenario
Understanding how attackers exploit default credentials helps organisations develop effective defences. This scenario demonstrates a typical attack progression:
Phase 1: Reconnaissance Attackers scan target networks to identify accessible devices and services. Port scanning reveals administrative interfaces on common ports. Device fingerprinting identifies specific models and associated default credentials.
Phase 2: Initial Access Automated tools test known default credentials against discovered interfaces. Successful authentication provides administrative access to target devices. Attackers document successful credentials for future exploitation attempts.
Phase 3: Lateral Movement Compromised devices become launching points for network exploration activities. Attackers enumerate additional systems using compromised credentials across network segments. Shared default passwords enable rapid network traversal.
Vulnerability Management and Detection
Effective vulnerability management requires systematic default credential identification and remediation. Organisations must maintain inventories of all network-connected devices and their authentication requirements. Regular security assessments help identify overlooked systems with unchanged credentials.
Automated scanning tools can detect default credentials across large network environments efficiently. These tools test common username and password combinations against discovered services. However, manual verification remains necessary for comprehensive coverage.
API penetration testing often reveals web-based interfaces using default authentication schemes. These interfaces may control critical infrastructure components or sensitive data repositories.
Detection Tools and Techniques
# Example Python script for default credential testing
import requests
from itertools import product
default_creds = [
('admin', 'admin'),
('root', 'password'),
('user', 'user')
]
def test_credentials(target_url, creds):
for username, password in creds:
try:
response = requests.post(
f"{target_url}/login",
data={'username': username, 'password': password},
timeout=5
)
if response.status_code == 200:
print(f"Success: {username}:{password}")
except requests.RequestException:
continueCommercial vulnerability scanners include default credential detection capabilities. These tools maintain updated databases of known credentials and device fingerprints. Regular scanning schedules help organisations maintain awareness of vulnerable systems.
Cybersecurity Best Practices for Credential Management
Implementing robust credential management practices prevents default password vulnerabilities effectively. Organisations should establish policies requiring immediate credential changes upon device deployment. These policies must apply to all network-connected systems without exception.
Strong password policies ensure replacement credentials meet security requirements appropriately. Passwords should include multiple character types and sufficient length for resistance against brute-force attacks. Password managers help administrators maintain unique credentials across numerous systems.
Regular password rotation schedules prevent long-term credential compromise scenarios. However, rotation frequency must balance security benefits against operational complexity. Many organisations find quarterly rotations provide adequate security without excessive administrative burden.
Hardening Systems Against Default Credential Attacks
System hardening involves multiple techniques for eliminating default credential vulnerabilities. Initial device configuration procedures should include mandatory credential changes. Automated deployment scripts can enforce these changes consistently across multiple devices.
Network segmentation limits the impact of compromised credentials significantly. Isolated network segments prevent lateral movement between compromised and secure systems. Micro-segmentation provides granular control over device-to-device communications.
Multi-factor authentication adds additional security layers beyond password-based authentication alone. SMS tokens, hardware keys, and biometric factors increase authentication security substantially. However, implementation complexity may limit applicability across all device types.
Configuration Management Examples
# Example router configuration commands
enable
configure terminal
username admin privilege 15 secret ComplexPassword123!
no username cisco
line vty 0 4
login local
transport input ssh
no transport input telnetAutomated configuration management tools ensure consistent security settings across device populations. Ansible, Puppet, and similar platforms can enforce credential policies systematically. These tools provide audit trails documenting configuration changes and compliance status.
Security Awareness and Training
Security awareness programmes must address default credential risks comprehensively. Technical staff require training on secure device deployment procedures. Management teams need understanding of business risks associated with unchanged default passwords.
Regular training sessions should cover emerging threats and updated best practices. Hands-on exercises help staff develop practical skills for identifying and remediating default credential vulnerabilities. Simulated attacks demonstrate real-world consequences of poor credential management.
Incident response procedures should include default credential assessment protocols. Teams must understand how to identify compromised systems and implement emergency credential changes. Documentation should specify escalation procedures for widespread compromise scenarios.
Training Programme Components
Effective training programmes combine theoretical knowledge with practical application exercises. Participants learn to identify vulnerable systems and implement appropriate remediation measures. Assessment activities verify knowledge retention and practical competency development.
Role-based training ensures relevant content delivery to different staff categories. Network administrators require detailed technical procedures for credential management. Security teams need comprehensive threat intelligence and incident response capabilities.
Ongoing awareness campaigns maintain focus on default credential risks throughout the organisation. Regular communications highlight recent attacks and evolving threat landscapes. Success stories demonstrate positive outcomes from proper credential management practices.
How Does Aardwolf Security Help?
Professional penetration testing companies like Aardwolf Security provide comprehensive default credential assessments for organisations worldwide. Our experienced team identifies vulnerable systems across complex network environments systematically.
Aardwolf Security’s penetration testing services include automated and manual default credential testing methodologies. We maintain current databases of manufacturer credentials and emerging vulnerability patterns. Our assessments provide detailed remediation guidance tailored to specific organisational requirements.
Our security experts work closely with client teams to develop practical remediation strategies. We provide training and consultation services supporting long-term security improvement initiatives. Contact our team to discuss your organisation’s default credential assessment requirements.
What Are Default Credentials?
Default credentials are factory-set usernames and passwords manufacturers install on devices before shipment. These credentials enable initial system access and configuration activities. Common examples include “admin/admin” and “root/password” combinations.
Manufacturers use default credentials to simplify initial device setup procedures. However, these credentials remain active until administrators change them manually. Many organisations fail to update these credentials, creating persistent security vulnerabilities.
Why Are Default Credentials Dangerous?
Default credentials create predictable attack vectors that cybercriminals exploit systematically. Attackers maintain comprehensive databases containing thousands of known default credential combinations. Automated tools can test these credentials against discovered systems rapidly.
The danger multiplies when organisations deploy multiple devices with identical default settings. Single compromised credentials can provide access to numerous systems simultaneously. This creates opportunities for widespread network compromise through minimal initial access.
How Do Attackers Find Systems with Default Credentials?
Attackers employ various techniques to identify systems using default credentials across target networks. Automated scanning tools probe common service ports for administrative interfaces. Device fingerprinting helps attackers identify specific models and associated default credentials.
Search engines like Shodan index internet-connected devices with accessible interfaces. Attackers can search these databases for specific device types or credential combinations. Social engineering attacks may also reveal information about deployed devices and their configurations.
What Types of Devices Commonly Use Default Credentials?
Network infrastructure devices frequently ship with default credentials for initial configuration purposes. Routers, switches, and wireless access points commonly use predictable username and password combinations. Industrial control systems and building automation devices also present default credential risks.
IoT devices represent particularly challenging default credential scenarios for modern organisations. Smart cameras, sensors, and controllers often lack robust security features. Many devices never receive security updates throughout their operational lifespans.
How Can Organisations Detect Default Credentials?
Organisations can employ automated scanning tools to identify systems using default credentials systematically. Commercial vulnerability scanners include default credential detection capabilities with updated credential databases. Manual testing may be necessary for comprehensive coverage across all system types.
Regular security assessments should include default credential verification procedures. Network inventories help identify all systems requiring credential verification activities. Penetration testing services provide professional assessment capabilities for complex environments.
What Are the Best Practices for Preventing Default Credential Attacks?
Establishing mandatory credential change policies prevents default password vulnerabilities effectively. These policies should apply to all network-connected devices without exception. Strong password requirements ensure replacement credentials meet appropriate security standards.
Automated deployment procedures can enforce credential changes during device installation consistently. Configuration management tools provide systematic approaches to credential policy enforcement. Regular auditing activities verify ongoing compliance with established security requirements.
Technical Glossary
Credential Stuffing: Automated attacks using lists of known usernames and passwords against multiple targets simultaneously.
Device Fingerprinting: Techniques for identifying specific device models and manufacturers through network reconnaissance activities.
Lateral Movement: Attack progression techniques enabling movement between compromised and additional target systems within networks.
Multi-factor Authentication: Security mechanisms requiring multiple authentication factors beyond passwords alone for system access.
Network Segmentation: Security architecture dividing networks into isolated segments to limit attack impact and lateral movement.
Vulnerability Management: Systematic processes for identifying, assessing, and remediating security vulnerabilities across organisational assets.
Further Reading
- NIST Cybersecurity Framework – Protect Function
- OWASP Authentication Cheat Sheet
- SANS Critical Security Controls
- NCSC Password Guidance