TLDR: Cloudflare successfully defended against a record-breaking 11.5 terabits per second DDoS attack that lasted just 35 seconds. The massive UDP flood originated primarily from compromised resources on Google Cloud Platform and set a new industry high for network bandwidth consumed by malicious traffic.
Table of Contents
Unprecedented DDoS Attack Scale Shattered Previous Records
Cloudflare blocked the largest DDoS attack ever recorded at 11.5 terabits per second (Tbps). This massive cyber assault lasted just 35 seconds but delivered unprecedented volumes of malicious traffic. The DDoS attack was characterised as a hyper-volumetric UDP flood that set a new industry high for network bandwidth consumed by malicious traffic.
Cloudflare’s security telemetry captured a sudden spike from negligible background noise to more than 11 Tbps in under 10 seconds. The attack demonstrates the evolving threat landscape organisations face today. Most of the attack came from compromised resources on the Google Cloud Platform, highlighting how cybercriminals exploit major cloud infrastructure.
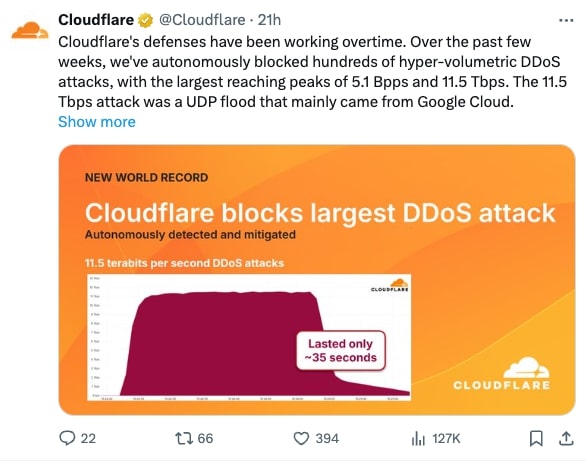
Credit: https://x.com/Cloudflare/status/1962559687368593552/photo/1
William Fieldhouse, Director of Aardwolf Security Ltd, comments: “This record-breaking DDoS attack demonstrates the evolving threat landscape organisations face today. The sheer scale and coordination required shows how cybercriminals are leveraging cloud infrastructure more effectively. Businesses need comprehensive network penetration testing services to identify vulnerabilities before attackers exploit them.”
Automated Defence Systems Stopped Attack Instantly
The company’s automated defense systems detected and neutralized the hyper-volumetric attack without requiring human intervention. Within moments, the company’s automated mitigation systems identified the abnormal flow of User Datagram Protocol (UDP) packets and applied targeted rate-limiting rules. This demonstrates the critical importance of autonomous security systems.
A graphic shared by Cloudflare revealed the striking lifecycle of the attack: a steep ascent to peak volume, followed by an immediate descent as mitigation engaged. Traditional manual incident response protocols cannot react swiftly enough to contain attacks that rise and fall within seconds. Modern threats require automated, cloud-scale security platforms.
Organisations must invest in similar automated defence capabilities. Professional penetration testing services help identify gaps in current security infrastructure. Regular assessments ensure businesses can withstand evolving cyber threats.
Cloud Platform Exploitation Highlights Infrastructure Risks
Detailed analysis from Cloudflare shows that the majority of the attack traffic was staged through compromised resources on the Google Cloud Platform. Public cloud platforms’ pay-as-you-go billing and virtually unlimited bandwidth make them attractive for threat actors seeking transient yet devastating surges of traffic. This exploitation method poses significant challenges for cloud security.
The attack’s origin from a major cloud provider demonstrates how criminals leverage legitimate infrastructure for malicious purposes. Industry experts caution that DDoS attacks are evolving in both scale and frequency. Cloud platforms provide the necessary resources for launching massive attacks whilst complicating attribution and takedown efforts.
Organisations using cloud services must implement robust security measures. Regular security assessments help identify potential vulnerabilities. Contact specialists for a pen test quote to evaluate your cloud security posture.
FAQ’s
What is the largest DDoS attack ever recorded?
The largest DDoS attack ever recorded reached 11.5 terabits per second (Tbps). Cloudflare successfully blocked this record-breaking attack, which originated primarily from compromised Google Cloud Platform resources. The attack lasted just 35 seconds but delivered unprecedented volumes of malicious traffic.
How long do most DDoS attacks last?
Most DDoS attacks are very short-lived. Research shows that 89% of network-layer DDoS attacks and 75% of HTTP attacks end within 10 minutes. Even the largest, record-breaking attacks can be extremely brief, such as the 35-second 11.5 Tbps attack. This short duration makes manual mitigation nearly impossible.
Can DDoS attacks be stopped automatically?
Yes, modern DDoS protection systems can detect and stop attacks automatically without human intervention. Cloudflare’s systems blocked the record-breaking 11.5 Tbps attack autonomously within seconds of detection. Automated systems are essential because attacks can rise and fall faster than humans can respond.
What is a hyper-volumetric DDoS attack?
A hyper-volumetric DDoS attack exceeds 1 terabit per second (Tbps), 1 billion packets per second, or 1 million requests per second. These massive attacks overwhelm traditional security equipment and require cloud-scale mitigation services. Cloudflare blocked over 6,500 such attacks in Q2 2025.
Why do attackers use cloud platforms for DDoS attacks?
Attackers exploit cloud platforms because they offer unlimited bandwidth through pay-as-you-go models, global infrastructure for distributed attacks, and legitimate traffic appearance that may bypass security filters. Cloud platforms also enable rapid scaling without upfront investment, making them attractive for cybercriminals.
How can businesses protect against large DDoS attacks?
Businesses should deploy cloud-based DDoS protection services with unlimited capacity, implement automated detection and response systems, use traffic analysis for rapid pattern recognition, and maintain distributed defence architectures. Regular penetration testing helps identify vulnerabilities before attackers exploit them.
What is the difference between UDP floods and other DDoS attacks?
UDP floods exploit the connectionless nature of the User Datagram Protocol to overwhelm targets with high-volume packets. Unlike TCP attacks that require connection establishment, UDP floods can immediately saturate network links. The 11.5 Tbps attack was primarily a UDP flood, making it particularly effective.
How much damage can a DDoS attack cause?
DDoS attacks can cause severe financial losses through service outages, customer churn, and reputation damage. Even “small” attacks under 1 Gbps can overwhelm unprotected servers. Large attacks targeting hosting providers affect multiple customers simultaneously, multiplying the impact and potential losses.
Are DDoS attacks increasing in frequency?
Yes, DDoS attacks are surging dramatically. Cloudflare blocked 20.5 million attacks in Q1 2025, representing a 358% year-over-year increase. The company has already blocked 27.8 million attacks in the first half of 2025, exceeding their entire 2024 total of 21.3 million attacks.
What should you do if your business suffers a DDoS attack?
If experiencing a DDoS attack, immediately contact your hosting provider or DDoS protection service, avoid making infrastructure changes during the attack, document the incident for investigation, and consider implementing automated protection for future threats. Professional security assessments can help prevent future attacks.