Cross-site scripting (XSS) attacks continue to plague web applications as one of the most prevalent security vulnerabilities in the digital landscape. According to the OWASP Top 10, XSS consistently ranks as a severe threat to modern web applications. In this comprehensive guide, we’ll explore what XSS attacks are, how they work, their potential impact on your business, and effective prevention techniques.
Table of Contents
What is Cross-Site Scripting (XSS)?
Cross-site scripting, commonly abbreviated as XSS, is a type of security vulnerability that enables attackers to inject malicious client-side scripts into web pages viewed by other users. When successful, an XSS attack allows a malicious actor to bypass same-origin policy—a critical security mechanism designed to prevent scripts from one website accessing data from another.
The name “cross-site scripting” reflects how these attacks work: the vulnerability allows code to be injected across sites, executing scripts in the browser of unsuspecting visitors. Unlike many cyber threats that target the application directly, XSS attacks primarily target the users of vulnerable websites.
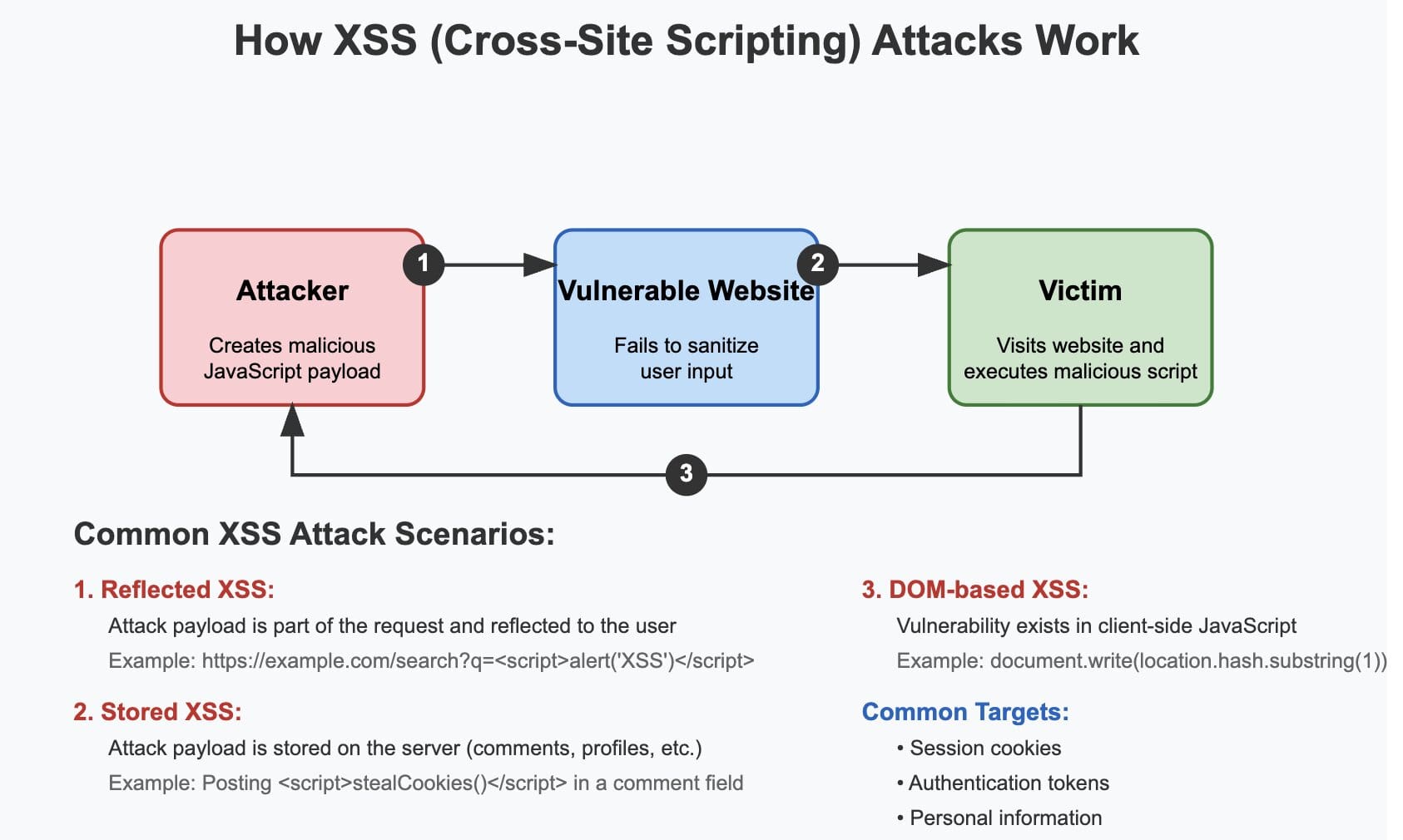
Types of XSS Attacks
Security professionals typically classify XSS attacks into three main categories, each with distinct characteristics and attack vectors:
1. Reflected XSS
Reflected XSS (also known as non-persistent XSS) occurs when malicious script is reflected off a web application to the victim’s browser. The attack is typically delivered through specially crafted links containing malicious code. When a user clicks on such a link, the script executes in their browser within the context of the targeted website.
For example, consider a search feature that displays your search term back to you without proper sanitisation:
https://example.com/search?term=<script>alert('XSS')</script>If the website directly includes this user input in its response without proper encoding, the script will execute in the user’s browser.
2. Stored XSS
Stored XSS (persistent XSS) occurs when the malicious script is permanently stored on the target server, such as in a database, message forum, comment field, or visitor log. When users browse to the affected page, the malicious script loads and executes automatically.
This type of XSS is particularly dangerous because:
- It doesn’t require user interaction with a special link
- It affects any visitor to the compromised page
- The attack continues until the malicious content is removed from the server
3. DOM-based XSS
DOM-based XSS exploits vulnerabilities in client-side scripts, modifying the page’s Document Object Model (DOM) environment in the victim’s browser. Unlike reflected or stored XSS, DOM-based XSS often doesn’t require the malicious payload to be sent to the server at all.
This attack unfolds entirely in the browser when client-side JavaScript code processes data from an untrusted source (like URL parameters) and inserts it into the DOM in an unsafe manner.
How Do XSS Attacks Work?
The fundamental mechanism behind all XSS attacks involves three key components:
- Input vector: A channel through which attacker-controlled data enters the application
- Vulnerability: Insufficient validation, sanitisation or encoding of user input
- Payload delivery: Exploitation that causes the victim’s browser to execute the malicious script
A typical XSS attack follows this sequence:
- The attacker identifies a vulnerable website that fails to properly validate or encode user input
- They craft a malicious payload containing JavaScript code designed to perform harmful actions
- The attacker delivers this payload to victims, either through direct links (reflected XSS), by storing it on the target site (stored XSS), or by manipulating the DOM (DOM-based XSS)
- When victims view the affected page, their browsers execute the malicious script in the context of the vulnerable site
- The script can then access cookies, session tokens, sensitive information or perform actions on behalf of the victim
What Damage Can XSS Attacks Cause?
Cross-site scripting vulnerabilities can lead to significant business impact and security breaches. Despite being client-side attacks, their consequences can be severe:
Account Compromise
XSS attacks can steal authentication cookies or session tokens, allowing attackers to hijack user accounts. This is particularly dangerous for administrative accounts, potentially giving attackers complete control over the application.
Data Theft
Malicious scripts can access sensitive data visible in the user’s browser, including personal information, financial details, and private communications. This data can then be transmitted to attacker-controlled servers.
Malware Distribution
XSS vulnerabilities can be leveraged to deliver malware to unsuspecting users, potentially leading to further system compromise beyond the browser.
Phishing Attacks
Attackers can modify the appearance of legitimate websites or inject fake login forms to harvest credentials. Because these phishing attempts occur on legitimate domains, they’re particularly convincing.
Defacement and Reputation Damage
XSS can be used to alter website content visible to users, potentially causing significant reputation damage, especially if offensive or misleading content is displayed.
Business Impact
Beyond the immediate technical consequences, organisations suffering from XSS vulnerabilities may face:
- Regulatory penalties for data protection failures
- Loss of customer trust
- Financial costs associated with incident response
- Potential legal liability for compromised user data
How Can You Prevent XSS Attacks?
Protecting your web applications from XSS vulnerabilities requires a multi-layered approach to security:
Input Validation and Sanitisation
Always validate and sanitise user input on the server side. This includes:
- Implementing strict input validation that accepts only expected format and rejects everything else
- Sanitising input by removing or encoding potentially dangerous characters
- Using allowlist approaches rather than blocklists for validation
Remember that client-side validation can be bypassed and should never be your only line of defence.
Output Encoding
Proper output encoding is crucial for preventing XSS. When displaying user-supplied content:
- HTML-encode data before inserting it into HTML element content
- Attribute-encode data before inserting it into HTML attributes
- JavaScript-encode data before inserting it into JavaScript data values
- CSS-encode data before inserting it into CSS values
- URL-encode data before inserting it into URL parameters
Use context-appropriate encoding for the specific part of the document where data is being inserted.
Content Security Policy (CSP)
Implement a strong Content Security Policy to reduce the risk and impact of XSS attacks. CSP allows you to specify which domains are trusted sources of scripts, styles, and other resources, preventing the execution of inline scripts and evaluations.
A basic CSP header might look like:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted-cdn.com;Use Modern Frameworks
Modern web frameworks like React, Angular, and Vue have built-in protections against XSS. They automatically escape variables in templates and provide mechanisms to safely handle HTML content. However, be aware that using certain features (like React’s dangerouslySetInnerHTML) can reintroduce XSS vulnerabilities.
HTTP Security Headers
Implement additional HTTP security headers to provide extra layers of protection:
- X-XSS-Protection – Enables built-in browser XSS filters
- X-Content-Type-Options – Prevents MIME-type sniffing
- Strict-Transport-Security – Enforces secure connections
Regular Security Testing
Conduct regular web application penetration testing and API penetration testing to identify and remediate XSS vulnerabilities before attackers can exploit them. Professional security assessments can uncover subtle XSS vulnerabilities that automated tools might miss.
What are real-world examples of XSS attacks?
Understanding historical XSS incidents helps illustrate the real-world impact these vulnerabilities can have:
The Samy Worm (2005)
One of the most famous XSS attacks was the Samy worm, which infected over one million MySpace profiles within 24 hours. Creator Samy Kamkar exploited an XSS vulnerability to create a self-propagating script that added “Samy is my hero” to users’ profiles and spread to visitors.
Twitter StalkDaily Worm (2009)
A stored XSS vulnerability in Twitter allowed the creation of a worm that forced users to retweet malicious content, rapidly spreading across the platform.
eBay XSS Vulnerability (2014)
eBay suffered from an XSS vulnerability that allowed attackers to create listings containing malicious JavaScript. When users viewed these listings, the script could steal their credentials and personal information.
How do I test for XSS vulnerabilities?
Testing for XSS vulnerabilities involves several approaches:
Manual Testing
Basic manual testing involves attempting to inject simple scripts into input fields and observing whether they execute. Common test strings include:
<script>alert('XSS');</script>
<img src="x" onerror="alert('XSS');">
javascript:alert('XSS')However, basic testing often misses more sophisticated vulnerabilities and context-specific issues.
Automated Scanning
Automated vulnerability scanners can help identify potential XSS issues, but they often produce false positives and may miss complex vulnerabilities. They’re best used as part of a broader security testing strategy.
Professional Penetration Testing
For comprehensive security assurance, professional web application penetration testing performed by skilled security professionals offers the most thorough approach to identifying XSS vulnerabilities.
Can WAFs protect against XSS attacks?
Web Application Firewalls (WAFs) can provide an additional layer of defence against XSS attacks, but they shouldn’t be your only protection:
- Benefits: WAFs can block known attack patterns and provide immediate protection while underlying vulnerabilities are being fixed
- Limitations: Sophisticated attackers can often bypass WAF protections through obfuscation and other evasion techniques
A robust security strategy combines WAF protection with secure coding practices, regular security testing, and proper input validation and output encoding.
How does XSS differ from other web vulnerabilities?
Cross-site scripting is often confused with other web vulnerabilities:
XSS vs. CSRF
While Cross-Site Request Forgery (CSRF) tricks users into performing unwanted actions on sites where they’re authenticated, XSS executes arbitrary code in the victim’s browser. CSRF exploits the trust a website has in a user’s browser, whereas XSS exploits the trust a user has in a particular website.
XSS vs. SQL Injection
SQL Injection attacks target the database layer by injecting malicious SQL statements, while XSS targets the client-side browser environment by injecting malicious scripts. SQL Injection can lead to data breaches on the server, while XSS primarily affects users of the application.
Conclusion: The Importance of XSS Prevention
Cross-site scripting remains one of the most widespread web application vulnerabilities despite being well-understood for over two decades. The persistence of XSS vulnerabilities is largely due to:
- The complexity of modern web applications
- The numerous contexts where user input might be processed
- Legacy code that wasn’t built with security in mind
- The increasing sophistication of XSS attack techniques
Protecting your applications requires consistent application of security best practices throughout the development lifecycle, from design and coding to testing and maintenance.
Secure Your Web Applications with Aardwolf Security
At Aardwolf Security, our experts specialise in identifying and helping you remediate cross-site scripting vulnerabilities through comprehensive web application penetration testing. Our thorough testing methodology goes beyond automated scanning to uncover even the most subtle XSS vulnerabilities that could put your business at risk.
Don’t wait until your organisation becomes the next XSS attack headline. Contact our security specialists today to schedule a consultation and take proactive steps to protect your web applications and your users.