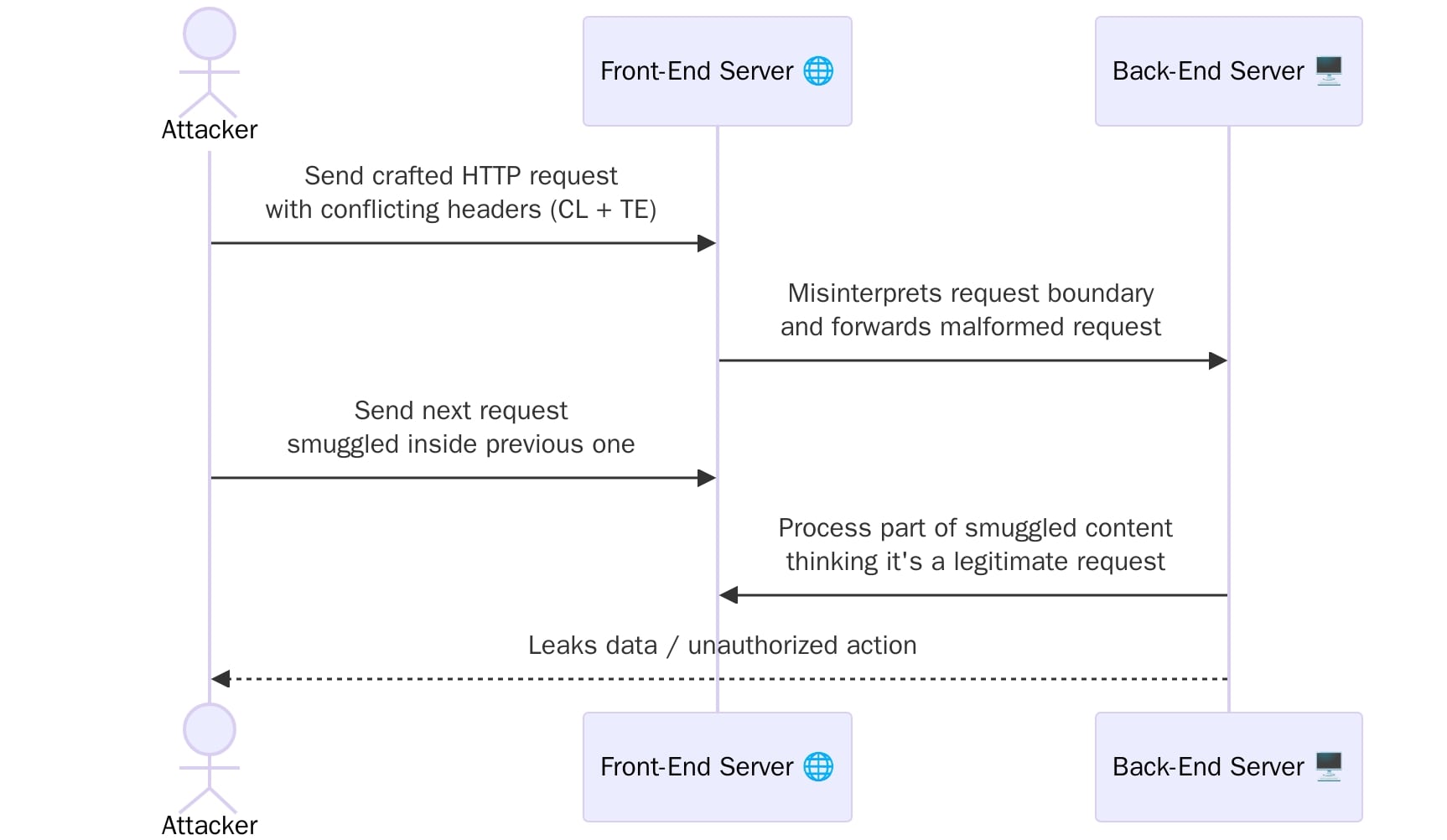
The debate over the best OS for penetration testing continues to divide the cybersecurity community. Kali Linux and Parrot Security OS stand as the two giants in this specialised field. Both offer robust toolsets designed for security professionals. The question remains: which best OS for penetration testing serves your testing needs better?
Professional security experts need reliable operating systems. These systems must provide comprehensive toolkits for vulnerability assessment. They must also maintain stability during critical security operations.
This article compares these leading security distributions in depth. We examine their features, performance, and practical applications. Our analysis helps you make an informed choice based on your specific testing requirements.
History and Development
Kali Linux: The Veteran Contender
Kali Linux emerged from the BackTrack project in 2013. Offensive Security developed this distribution as a complete rebuild. They based it on Debian’s solid foundation rather than Ubuntu.
The name “Kali” derives from a Hindu goddess associated with time and change. This symbolism reflects the destructive-yet-regenerative nature of security testing. Kali quickly became the industry standard.
Offensive Security maintains Kali with regular updates. They focus on providing security professionals with reliable tools. Their development cycle prioritises stability alongside cutting-edge features.
Parrot Security OS: The Progressive Alternative
Parrot Security OS appeared in 2013 as a Frozenbox project. Lorenzo Faletra initiated this Debian-based distribution with different priorities. He focused on creating a lighter, more versatile system.
The development team grew into the Parrot Project community. They emphasise accessibility and efficiency. Their approach makes advanced security tools available on modest hardware.
Parrot has evolved beyond security testing. It now offers specialised editions for different use cases. These include security, home/work productivity, and embedded systems applications.
Core Features Comparison: Best OS for Penetration Testing Features
Kali Linux: Toolset and Environment
Kali comes with over 600 pre-installed penetration testing tools. These cover everything from information gathering to exploitation. The distribution organises tools logically by category.
The Xfce desktop environment provides Kali’s default interface. Users can choose alternative environments during installation. These options include GNOME, KDE, and MATE.
Kali offers specialised configurations for various scenarios. These include cloud deployments, ARM devices, and forensic investigations. The operating system supports both persistent and live boot options.
Parrot Security OS: Toolset and Environment
Parrot provides approximately 500 security tools. Its selection focuses on quality and efficiency. The distribution includes unique tools alongside industry standards.
The MATE desktop environment creates Parrot’s lightweight interface. This environment ensures responsiveness even on older hardware. The system features Firejail for application sandboxing.
Parrot offers three main editions: Security, Home, and IoT/Embedded. Each serves different user needs with tailored configurations. The Security edition focuses specifically on penetration testing requirements.
Direct Comparison of Key Features
| Feature | Kali Linux | Parrot Security OS |
|---|---|---|
| Base System | Debian | Debian |
| Default Desktop | Xfce | MATE |
| RAM Usage (Idle) | 500-700MB | 350-500MB |
| Default Browser | Firefox | Firefox |
| Default Tools | ~600 | ~500 |
| Anonymous Mode | Available | Integrated |
| Minimum System Requirements | 2GB RAM, 20GB Storage | 1GB RAM, 16GB Storage |
| Release Cycle | Rolling | Rolling |
| Community Size | Very Large | Large |
| Corporate Backing | Offensive Security | Community-driven |
Performance and Resource Usage: How the Best OS for Penetration Testing Performs
System Requirements
Kali Linux demands slightly more resources for optimal performance. The official requirements specify 2GB RAM minimum. They recommend 20GB storage space for full installation.
Parrot OS runs effectively on lighter systems. It requires only 1GB RAM for basic functionality. The system needs 16GB storage space for complete installation.
Both distributions can function on older hardware. Parrot generally performs better in resource-constrained environments. Kali prioritises tool availability over minimal resource usage.
Boot Times and Responsiveness
Kali Linux boots relatively quickly on modern systems. The startup process typically completes in 30-45 seconds. Desktop responsiveness depends on the chosen environment.
Parrot OS demonstrates faster boot times in most tests. The system typically starts in 25-35 seconds. Its MATE desktop remains responsive even during intensive operations.
Resource monitoring shows lower memory usage for Parrot. The difference becomes more significant during multitasking. This efficiency makes Parrot suitable for virtual machine deployments.
Tool Performance
Kali’s tools benefit from extensive optimisation. The distribution provides stable performance during intensive tests. Resource-heavy applications like Metasploit run reliably.
Parrot balances performance with efficiency. Its tools operate with lower resource overhead. This approach suits environments with limited computing power.
Testing complex exploits shows comparable success rates. Both systems handle most security tasks effectively. Performance differences appear mainly in resource utilisation rather than capability.
Tool Availability and Management in the Best OS for Penetration Testing
Package Management Systems
Kali uses the APT package manager with custom repositories. This system provides access to security-focused packages. The distribution includes the following command for tool installation:
sudo apt update && sudo apt install [tool-name]Parrot also employs APT with its own repositories. The system integrates the Synaptic package manager. Users can install tools through commands or graphical interfaces:
sudo apt update && sudo apt install [tool-name]Both distributions maintain dedicated repositories. These contain security tools not found in standard Debian sources. Both systems support custom repository configuration.
Unique Tools Comparison
Kali includes several exclusive tools. These include Offensive Security’s own developments. Examples include:
# Running Kali's exclusive tools
sudo armitage
sudo beef-xss
sudo set (Social-Engineer Toolkit)Parrot offers unique utilities not found in Kali. These focus on anonymity and cryptography. Examples include:
# Running Parrot's exclusive tools
sudo anonsurf start
sudo cryptsetup-nuke-password
sudo mat2The overlap between toolsets reaches approximately 80%. Most industry-standard tools appear in both distributions. These include Metasploit, Wireshark, and Burp Suite.
Ease of Use and Learning Curve
Installation Process
Kali provides a straightforward installation wizard. The process offers various configuration options. These include desktop environment selection and tool presets.
Parrot features a similar installer with added flexibility. The system allows more granular component selection. This helps create minimal installations for specific purposes.
Both systems support live boot environments. These allow testing without permanent installation. Both also offer persistence options for maintaining changes across reboots.
Documentation and Community Support
Kali maintains extensive official documentation. Offensive Security provides professional training materials. The large community offers solutions for most issues.
Parrot’s documentation continues to expand. The community actively contributes tutorials and guides. Official resources cover core functionality comprehensively.
Online forums show more activity for Kali-related questions. The distribution’s longer history creates deeper knowledge bases. Parrot users still find adequate support through dedicated channels.
Learning Resources
Kali integrates with Offensive Security courses. These include the famous OSCP certification. The alignment creates a smooth learning path for professionals.
Parrot emphasises educational usage alongside professional applications. The distribution includes documentation aimed at beginners. Its approach makes security concepts more accessible.
Both systems provide internal documentation through man pages. They also include tool-specific help commands. These resources help users learn individual applications.
Security and Privacy Features
Anonymous Mode and Privacy Tools
Kali offers optional anonymity features. Users can install and configure privacy tools. The process requires manual setup in most cases.
Parrot integrates the AnonSurf tool by default. This system routes traffic through Tor with one command:
sudo anonsurf startBoth distributions support VPN configurations. They include tools for encrypted communications. Parrot emphasises privacy features more prominently in its default configuration.
System Hardening
Kali runs with root privileges by default in older versions. Newer versions use standard user accounts. The system requires manual hardening for production environments.
Parrot implements security measures by default. The system uses firejail for application sandboxing. It provides securised defaults for common operations.
Both distributions receive regular security updates. They patch vulnerabilities promptly through their repositories. Both require proper configuration for maximum security.
Update Frequency and Security Patches
Kali follows a rolling release model with frequent updates. Critical security patches appear quickly after disclosure. The update command remains simple:
sudo apt update && sudo apt full-upgradeParrot maintains a similar update schedule. Its rolling release model ensures current security patches. The system employs standard Debian update mechanisms:
sudo apt update && sudo apt dist-upgradeBoth distributions prioritise security-related updates. They maintain current versions of critical tools. Neither sacrifices security for stability in update policies.
Specialised Use Cases for the Best OS for Penetration Testing
Forensics Applications
Kali includes dedicated forensic tools. These support evidence collection and analysis. The distribution offers a specific forensic mode that prevents drive mounting:
# Boot parameter for forensic mode
forensic noswap noautomountParrot provides comparable forensic capabilities. Its tools focus on maintaining evidence integrity. The system includes write-blocking mechanisms for safe analysis.
Digital investigators can use either system effectively. Both support common forensic workflows. They include tools for memory analysis, disk imaging, and data recovery.
Wireless Security Testing
Kali excels at wireless network assessment. It includes numerous tools for WiFi testing. The system supports various wireless hardware through comprehensive drivers.
Parrot matches this capability with its wireless toolkit. The distribution includes drivers for most testing devices. Its tools support modern wireless security protocol analysis.
Both systems handle common wireless attacks. They support packet injection with compatible hardware. Both include tools for WPA/WPA2/WPA3 assessment.
Web Application Testing
Kali provides comprehensive web application testing tools. These include proxies, scanners, and exploitation frameworks. The distribution supports complex web security assessments.
Parrot offers similar web testing capabilities. Its tools cover vulnerability scanning and exploitation. The system includes browsers configured for security testing.
Both distributions support OWASP methodology implementation. When evaluating the best OS for penetration testing for web applications, both include tools for testing all common web vulnerabilities. Performance differences in web testing remain minimal.
FAQ About the Best OS for Penetration Testing: Kali Linux and Parrot OS
Which is better for pen testing: Kali or Parrot?
The answer depends on your specific needs. Kali offers more pre-installed tools and larger community support. Parrot provides better performance on limited hardware and enhanced privacy features.
Your experience level also matters in this choice. Beginners might appreciate Parrot’s more accessible interface. Professionals often prefer Kali’s comprehensive toolset and compatibility.
Consider your hardware constraints when deciding which is the best OS for penetration testing for your needs. Parrot performs better on systems with limited resources. Kali works optimally on modern hardware with sufficient RAM.
Can I run Kali or Parrot on a virtual machine?
Yes, both distributions run effectively in virtual environments. They support major virtualisation platforms like VirtualBox, VMware, and Hyper-V.
Parrot generally requires fewer resources when virtualised. This makes it suitable for systems with limited RAM. Kali’s higher resource requirements may affect performance in virtual machines.
Both distributions offer pre-built virtual machine images. These simplify the setup process considerably. Both support snapshot features for testing potentially damaging operations.
Are Kali and Parrot legal to use?
Both distributions are completely legal to download and use. The legality concerns arise from how you use these tools, not the software itself.
Using either system for unauthorised penetration testing is illegal. Always obtain proper written permission before testing any system. Follow responsible disclosure practices for any vulnerabilities discovered.
Many security professionals use these distributions daily. They conduct authorised security assessments with proper scope definitions. Educational use also remains perfectly legal in most jurisdictions.
Do I need to be an expert to use these operating systems?
No, but some technical knowledge helps considerably. Both systems assume basic Linux familiarity. They expect users to understand fundamental security concepts.
Beginners can learn effectively with either distribution. Parrot offers a slightly gentler learning curve. Kali provides more comprehensive documentation and training resources.
Both communities welcome newcomers with questions. Many online tutorials cover basic operations. Starting with a virtual machine installation reduces risk for new users.
How often should I update Kali or Parrot?
Security professionals should update these systems before each use. Both distributions receive frequent security patches. Running outdated versions may miss critical tool updates.
The rolling release model ensures constant improvements. Update commands remain simple in both systems. Regular updates prevent tool compatibility issues during assessments.
Consider keeping separate installations for stability. Test updates on non-critical systems first. This approach prevents update-related issues during important security assessments.
Practical Scenario: Using the Best OS for Penetration Testing in Web Application Assessment
Step-by-Step Setup Process
- Install your chosen distribution (Kali or Parrot) on your testing system.
- Update the system to ensure all tools contain the latest versions:
# For both Kali and Parrot sudo apt update && sudo apt upgrade -y - Install additional web testing tools if needed:
# For both Kali and Parrot sudo apt install burpsuite zaproxy sqlmap dirb nikto -y - Configure your browser proxy settings for interception:
# Firefox proxy settings Preferences > Network Settings > Manual proxy configuration HTTP Proxy: 127.0.0.1 Port: 8080 - Start your proxy tool and configure it for interception:
# Starting Burp Suite sudo burpsuite # Configure proxy listener in Burp Proxy > Options > Add > Bind to port: 8080 - Begin testing the target web application through your intercepting proxy.
Both Kali and Parrot handle this workflow efficiently. The process remains nearly identical on either system. Tool functionality operates consistently across distributions.
Conclusion: Making Your Choice
The best OS for penetration testing ultimately depends on your specific requirements. Both Kali Linux and Parrot Security OS offer exceptional capabilities for security professionals.
Choose Kali Linux if you prioritise comprehensive tool availability. Select it if you have modern hardware with sufficient resources. Pick it when extensive community support matters most.
Choose Parrot OS if you need efficiency with limited resources. Select it when privacy features hold particular importance. Pick it for its balanced approach to security and usability.
Many professionals maintain both systems for different scenarios. They use Kali for feature-complete assessments. They deploy Parrot for lightweight testing or privacy-focused operations.
Whichever system you choose, responsible usage remains essential. These powerful tools require ethical application. They serve to improve security rather than compromise it.
Professional Penetration Testing Services
Need expert security assessment rather than conducting it yourself? Aardwolf Security provides comprehensive penetration testing services delivered by certified professionals.
Our team uses both Kali Linux and Parrot OS alongside proprietary tools. We tailor our approach to your specific security requirements. Our methodology follows industry best practices.
Aardwolf Security helps organisations identify vulnerabilities before attackers exploit them. Our detailed reports include practical remediation advice. We support your security improvement journey.
Contact us today to discuss your security testing needs. Our experts will develop a customised assessment plan. Reach out to our team for a confidential consultation.
Glossary of Technical Terms
- Penetration Testing: Authorised simulation of cyberattacks to identify security vulnerabilities.
- Live Boot: Running an operating system from removable media without installation.
- Rolling Release: Continuous update model rather than version-based releases.
- Persistence: Maintaining changes across reboots when using live media.
- APT: Advanced Package Tool, the package management system used by Debian-based distributions.
- Sandbox: Isolated environment for running applications with limited system access.
- Write-Blocking: Technique preventing data modification during forensic analysis.
- Proxy Interception: Capturing and modifying web traffic between browser and server.